Introduction
HaloENGINE is a Java-based classification engine that applies business logic and integrates with the Microsoft Purview Information Protection service to fetch the sensitivity labels for configuration in the admin portal. Using metadata, it classifies and organizes data while enforcing schemas and action rules, serving as the core component that works with the HaloCAD for PLM/PDM solution to protect data.
The HaloCAD for PLM solution integrates with the PLM application, includes HaloCAD PROTECT and HaloCAD MONITOR features, and leverages Microsoft Purview Information Protection (MPIP), formerly Microsoft Information Protection (MIP), to provide Enterprise Digital Rights Management (EDRM). During file download, HaloENGINE receives relevant metadata from HaloCAD for PLM/PDM, determines the appropriate action based on the configured rules, and forwards the label and action information to HaloCAD for PLM/PDM for file processing (encryption).
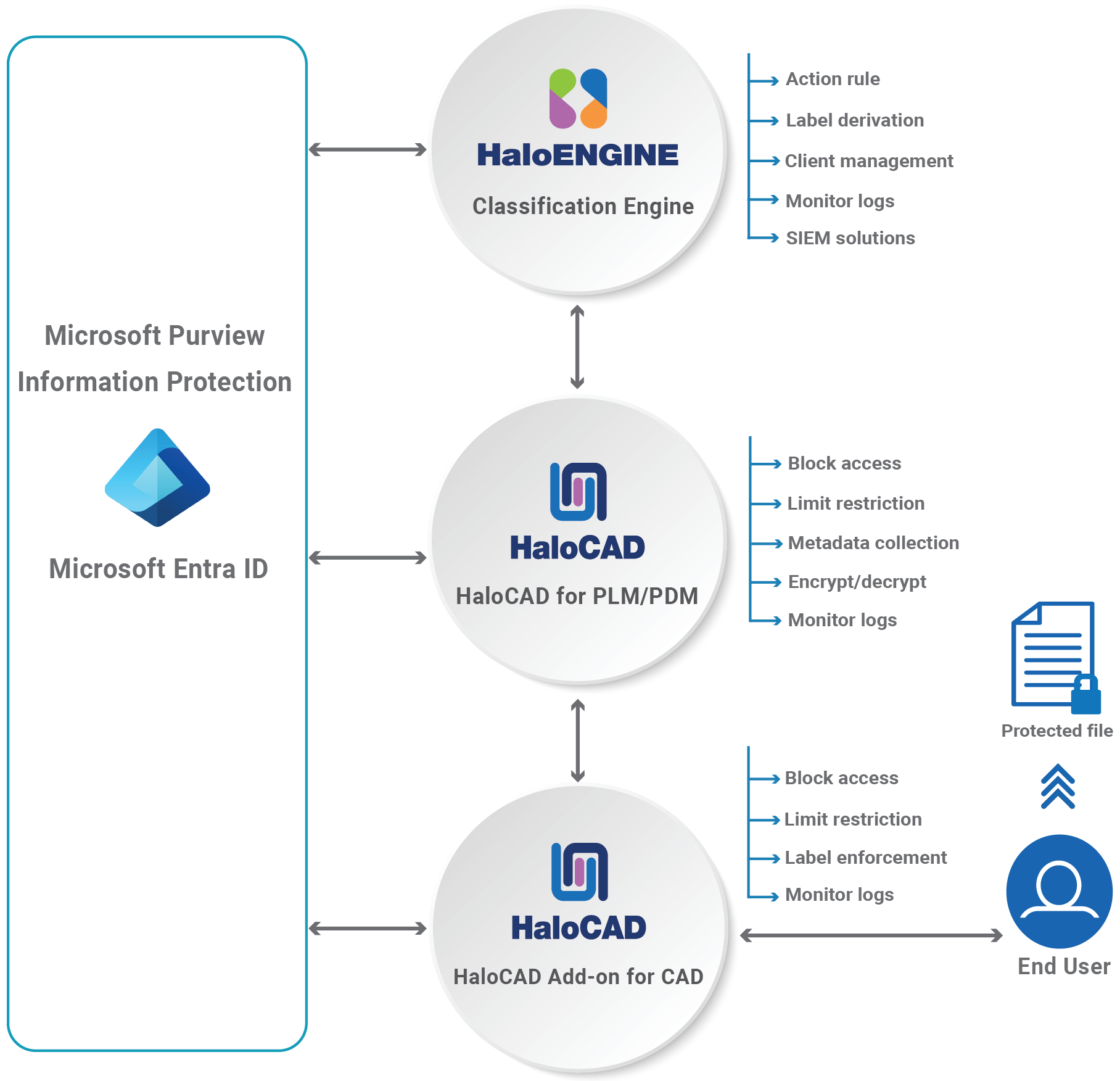
HaloENGINE with HaloCAD for PLM solution
HaloENGINE Features
-
Business logic: All business logic decisions are handled by this classification engine.
-
Logging the audit logs: Captures any file uploaded or downloaded, regardless of file protection.
-
Supports SIEM solutions, including Microsoft Azure Sentinel, Splunk, RSA, and others.
-
Halochain: Verifies whether the log file has been tampered with or not.
-
Dashboard: Displays important performance indicators and metrics, providing an overview of the company's data upload and download events.
About this Manual
This manual will guide you through the installation and configuration of the following components:
-
HaloENGINE
-
HaloENGINE API
About the Term “HaloENGINE Tomcat Service”
The HaloENGINE Tomcat Service is a common component used in both the HaloENGINE and HaloCAD products. Since it was initially developed for HaloENGINE and later adopted across HaloCAD, all Tomcat instances in Secude appear under the name “HaloENGINE Tomcat Service.”
General Concepts of Classification
Sensitive Data Classification: This is the process of identifying and categorizing all the data in an organization depending on its sensitivity. When a systematic method of data classification is used, sensitive information is adequately protected and made accessible to those who need it. For example, more sensitive data, such as financial information, might be categorized in such a way that disclosure carries a higher risk. General information, such as that utilized for marketing, would be categorized as a lower risk. A higher level of protection is necessary for data identified as having a higher risk, whereas lower-risk data may need proportionately less protection. A data classification schema describes a specific approach to determining data classification levels.
Levels of Sensitive Data
Depending on sensitivity, data is typically categorized into several kinds.
-
Public: low data sensitivity
-
Internal: moderate data sensitivity
-
Confidential: high data sensitivity
You can take suitable action on the appropriate content in this situation with the use of Microsoft Purview's sensitivity labels. Sensitivity labels allow you to identify the level of sensitivity of data across your organization and impose protective settings that are appropriate for the sensitivity of that data.
How are labels created?
Through the Microsoft Purview portal, you can administer how labels are published to your users. For more details, please refer to Microsoft's online documentation.
Classification Scheme
It takes meticulous planning and preparation to define a classification scheme for an organization and set information types and labels. Each organization is unique, and there are no one-size-fits-all data protection rules. You could design your classification scheme based on the business context. Throughout this chapter, a basic-level scenario is used to demonstrate the configuration classification engine. Classifying data can be done in various ways, but most businesses prefer to use a three-level classification schema: Public, Internal, and Confidential.
Best Practices
When creating classification labels, consider the following recommendations:
-
Leverage existing classification schemas (if available):
Reuse established frameworks within your organization to maintain consistency and reduce redundancy. -
Use sub-labels for key departments:
Certain departments may have unique classification requirements. Create sub-labels to address these specific needs. For example, Finance-Confidential, HR-Confidential. -
Choose meaningful label names:
Avoid using acronyms or ambiguous terms. Ensure label names clearly reflect their purpose and meaning.
Consider the following naming examples for the Sensitivity property:
-
Personal – Non-business data for personal use only.
-
Public – Information intended for public release, such as marketing materials or press announcements.
-
Confidential – Sensitive business data that could cause harm if shared with unauthorized individuals. Examples: contracts, security reports, sales data.
-
Secret – Highly sensitive business data that could cause significant damage if shared without authorization. Examples: customer information, contract letters, unreleased financial reports.
Classification Rule Engine
This is where HaloENGINE's business logic resides. It comprises the following:
-
Classification Schema - Defines which data categories will be used to categorize the organization's data.
-
Classification Rules - Rules are defined based on metadata and action rules to determine whether to block, label, protect, or decrypt a file.
Use the table below to decide how you want to deploy the features.
|
Actions |
Description |
|---|---|
|
Monitor |
File uploads and downloads are audited. |
|
Block |
File uploads and downloads are blocked. |
|
Label/Protect |
File uploads and downloads are classified. Using appropriate MPIP labels, classification labels are embedded in the file metadata. |
Action description
Quick Start Installation Summary
The following visual illustrates the high-level concept of configuring HaloENGINE with HaloCAD.
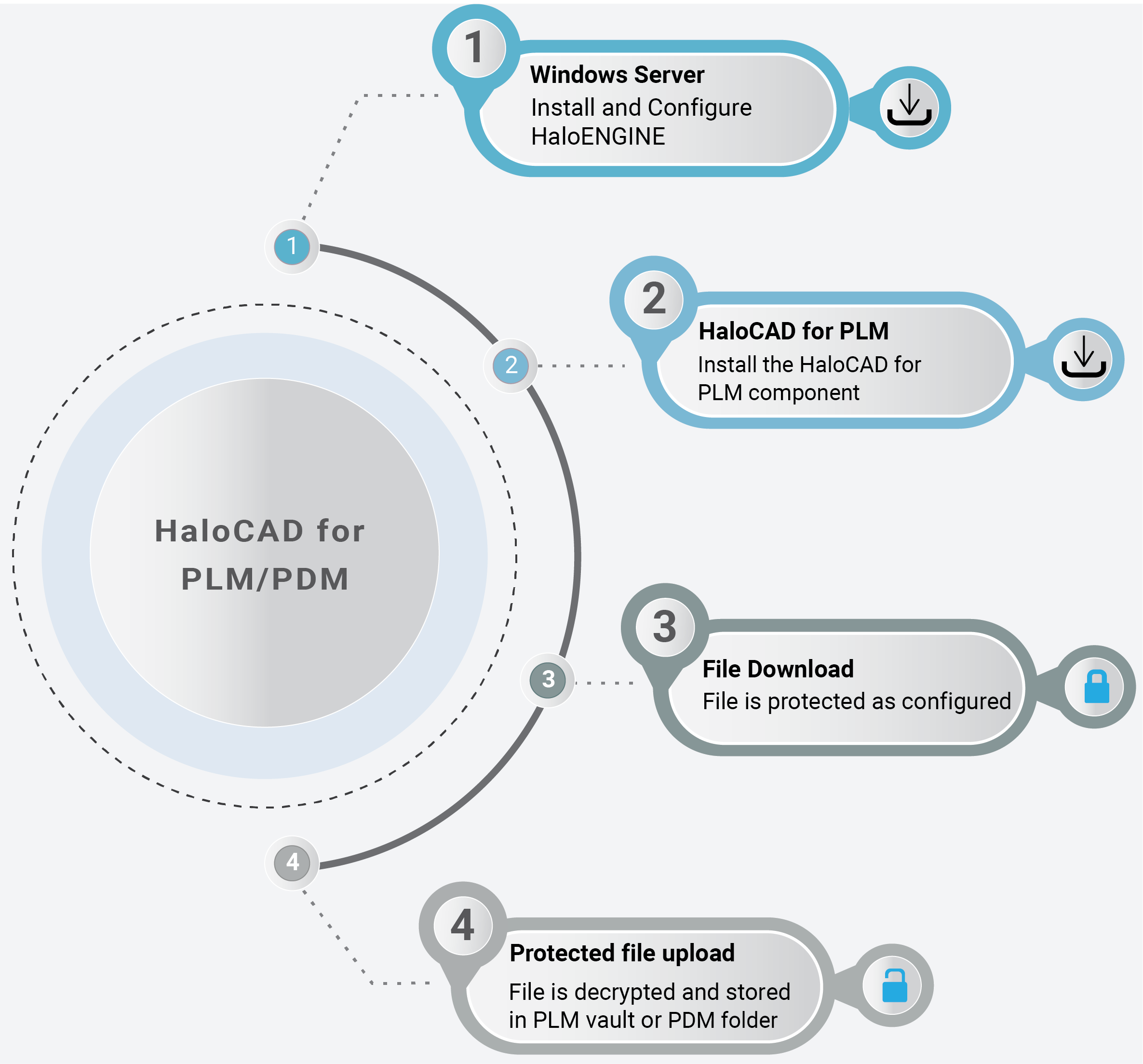
Quick start installation steps
Reference Manuals
The table below describes where to obtain information.
|
Component |
Refer to |
|---|---|
|
Step 1 – How to install and configure HaloENGINE. |
Refer to the current manual. |
|
Step 2 – How to install HaloCAD for PLM/PDM. |
Please refer to the respective HaloCAD for the PLM/PDM Installation Manual you have purchased |
|
Steps 3 and 4 – Workflow illustrating protection and decryption |
Please refer to the respective HaloCAD for the PLM/PDM Operations Manual you have purchased |
Reference Manuals
How does it work?
At a high level, the workflow between HaloCAD for PLM and HaloENGINE is illustrated in the following steps:
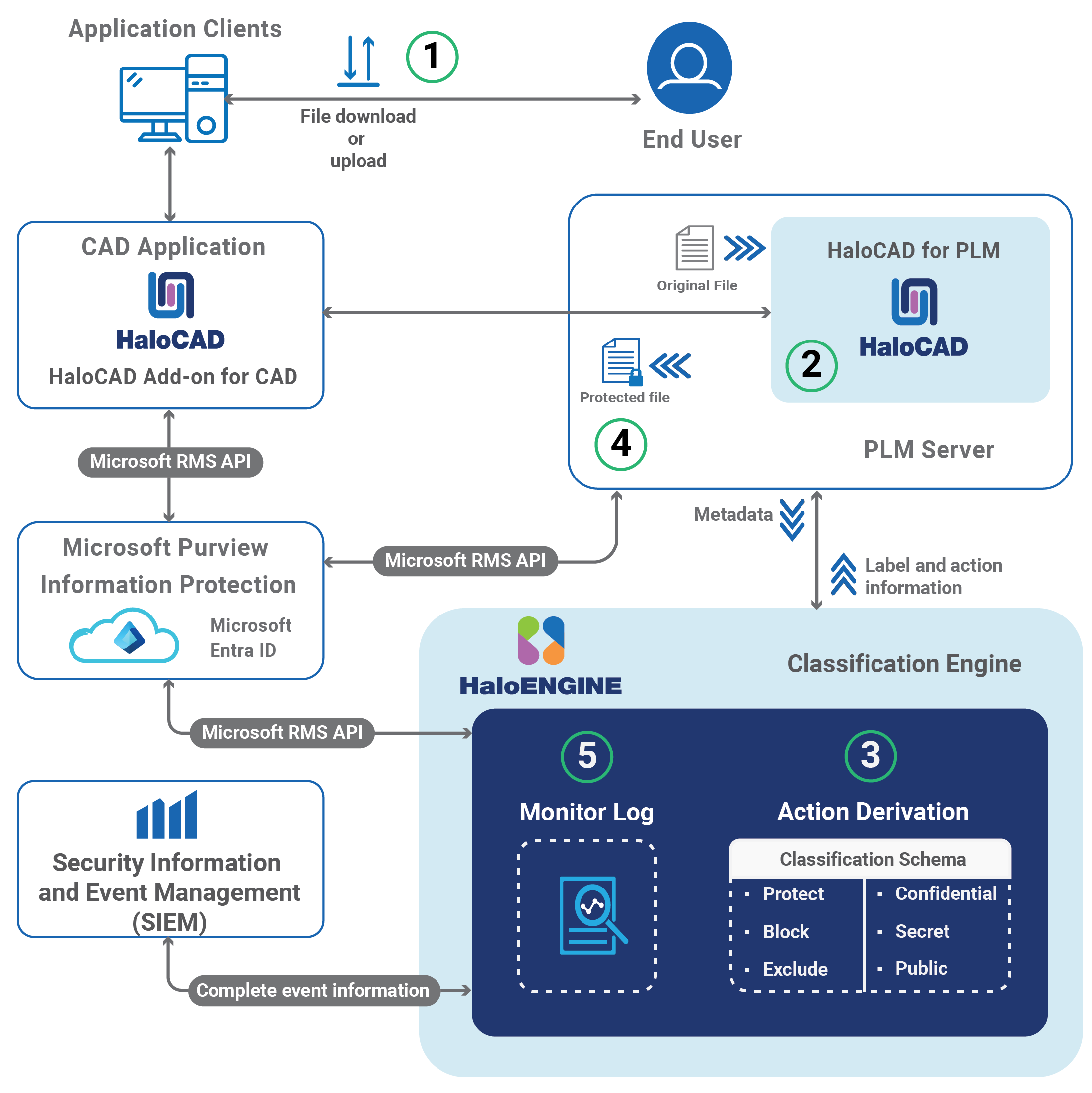
Integration Workflow: HaloCAD for PLM and HaloENGINE
-
The user performs a check-out (download) or check-in (upload) action.
-
HaloCAD for PLM fetches the user-selected file and collects its metadata. The metadata is sent to the HaloENGINE, where the appropriate action and label information are derived and provided back to HaloCAD for PLM.
-
HaloCAD for PLM executes actions based on the derived action and label information:
-
If no valid action is available, the file is downloaded without modification.
-
During check-in, if a valid action with a label is found, HaloCAD for PLM removes the label and stores the decrypted file in PLM.
-
During check-out, if a valid action with a label is found, HaloCAD for PLM applies the label.
-
If a block action rule is configured in HaloENGINE, HaloCAD for PLM prevents file downloads.
-
-
The protected file is returned to the user.
-
HaloCAD for PLM captures the event details and forwards them to the HaloENGINE monitor log for auditing.
