Using the configuration tool, you can quickly set up the HaloSHARE.
License Activation
A license for a product is necessary for access to features and support, legal compliance, security, and reliability. The primary Secude licensing method uses a Key-based license that regulates and allows access to the application's features. Therefore, to enable features, we suggest obtaining the license key from Secude support before installing the HaloSHARE.
Key-based License
Upon purchase or registration with Secude, a special "license key" is provided to the user to control the use of the application. After installing the service, the administrator must enter the license key, which is an alphanumeric code, in the configuration tool to activate the license. By entering this key, the entire functionality of HaloSHARE is unlocked, and the user's authorization to use it is validated.
This document does not cover all the specifics of purchasing a license. Please contact Secude’s representative for additional details.
To complete the license activation, carry out the following steps:
-
Navigate to the destination folder you specified during installation. The default folder is
C:\Program Files\Secude\HaloSHARE. -
Run the program
HaloSHAREConfiguration.exewith Run as Administrator permission. -
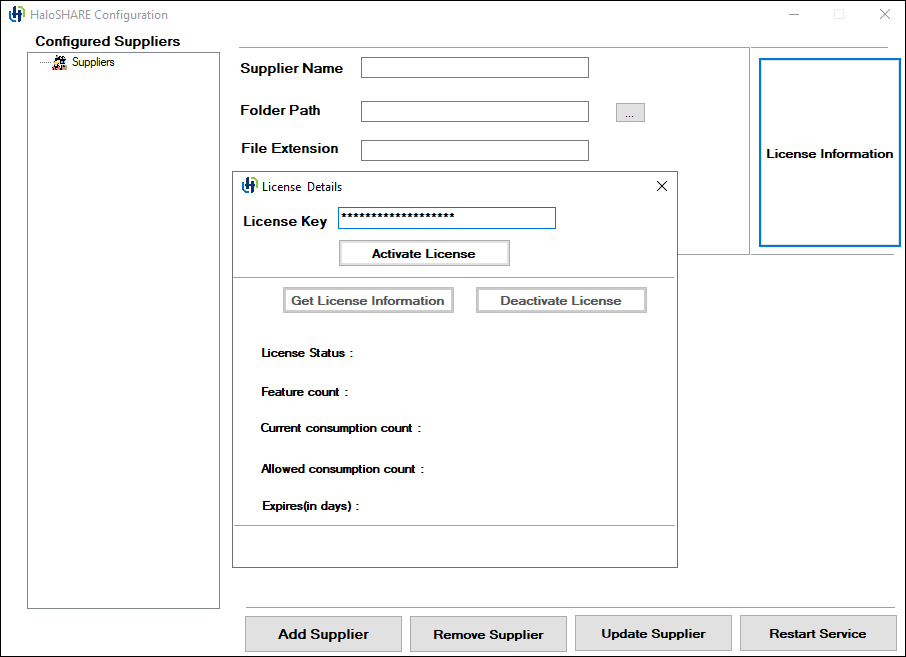
The HaloSHARE Configuration screen will appear, and on the configuration screen, click License Information.
-
The License Details screen will appear as shown below:
HaloSHARE Configuration screen
-
Enter the license key provided to you by Secude and click Activate License.
-
Please be patient while the license key activation is completed.
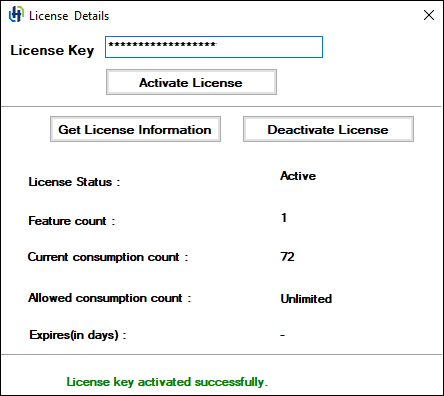
License Information
-
You will receive a confirmation message after successfully activating the license.
-
You will automatically receive detailed license information only the first time you activate the license. However, you can get the details at any time by clicking Get License Information.
-
If the License Status is Active, it means you entered a valid license key, whereas a license error means you entered an incorrect license key.
-
-
Related tasks:
-
License Deactivation: Administrators may deactivate a HaloSHARE license for a variety of reasons, based on your organization's standards and specific scenarios. To do so, click on Deactivate License.
-
Please note that a license is deactivated automatically if HaloSHARE is uninstalled.
-
If your license expires, enter a new license and click Update License, or activate it using the tool
hsadm.exe. For more details, refer to the section “Service Configuration using Admin Tool”.
-
Supplier Configuration
HaloSHARE can encrypt files with either a Static Permission label or a Custom Permission.
Difference between Basic/Static Permission Labels and Custom Permissions
Static Permission Labels - These are sensitivity labels in which the administrator defines the permission set while defining the labels in the Microsoft Purview portal.
Custom Permissions - This is a list of permissions available for user selection in the HaloSHARE application UI. They are also known as user-defined permissions.
Quick Start on Configured Suppliers
The Configured Suppliers pane on the right side of the screen on the configuration tool displays a supplier and the folder path with whom you have shared sensitive business data. For example, if “Prestin Engineering” is a supplier and C:\Prestin Engineering is the source path where you store Prestin-related business data internally. Additionally, to share it with Prestin representatives in a shared folder, you would have a destination folder where files are copied from the source. You can configure similarly with different source and destination folders for other suppliers, such as "Manifold Dynamics" and "Oriental Construction".
-
File overwriting occurs when the same file is moved repeatedly to the same source folder.
-
Case 1: Without the Move to Destination Path option.
For example, suppose the source folder is configured with the text file extension and Move to Destination Path is not selected. Copy a text file (
sample.txt) into the source folder. The file is encrypted and namedsample.ptxt. If you place the same (sample.txt) file back into the source folder, the existingsample.ptxtis overwritten. -
Case 2: With the Move to Destination Path option.
In this case, when a file is moved to the source folder, it is encrypted and sent to the destination folder. When you place the same file in the source folder, it is considered a new file, encrypted, overwritten, and moved to the destination folder.
-
-
It is not allowed to set the same folder or subfolder path for more than one supplier.
-
Both the OneDrive service and our HaloSHARE service cannot access the same file at the same time. There will be an access violation or access denied error.
How to Configure HaloSHARE
Follow the steps below to configure HaloSHARE:
-
Navigate to the destination folder you specified during installation. The default folder is
C:\Program Files\Secude\HaloSHARE. -
Double-click on the
HaloSHAREConfiguration.exefile. -
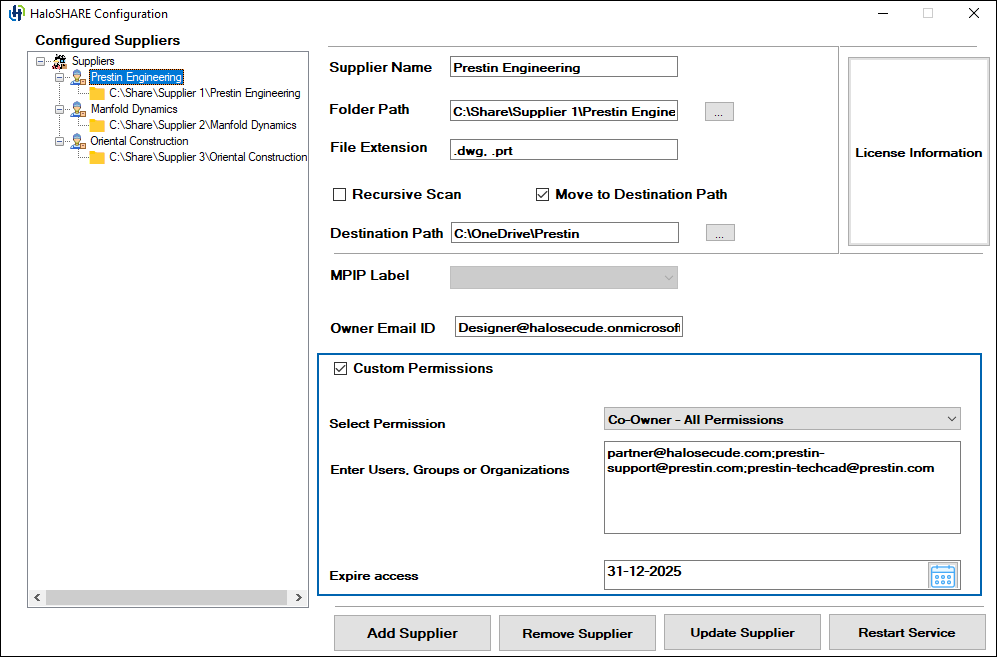
The HaloSHARE Configuration screen will appear as shown below:
HaloSHARE screen
-
Enter the supplier's name in the Supplier Name box, whose files must be protected. For example,
Prestin Engineering -
Click the Browse button next to the Folder Path to select the source folder that HaloSHARE should monitor. For example,
C:\Supplier 1\Prestin Engineering -
Enter the file extension in the File Extension box. By defining the extensions, protection will only apply to the specified file extension, leaving other files in the source folder unencrypted. For example,
.dwg,.prt. Note: If you mention asterisk symbol (*) the following files will be included by default for protection.prt,.asm,.sec,.frm,.drw,.lay,.cem,.mfg,.neu, and.log. You may also add Creo file formats along with iteration. For example,.prt.1. -
Select the Recursive Scan option to scan all subfolders within the source folder and encrypt the files within them. If this option is not selected, encryption is only performed on the source folder.
-
Select the Move to Destination Path option to move the encrypted files from the source folder to the destination folder. The destination folder can be another shared folder where you store files for external access, such as those associated with a supplier, vendor, or external consultant. For example, the destination folder could be a OneDrive folder.
-
Click the Browse button next to the Destination Path to select the destination folder. HaloSHARE will copy the encrypted files to this destination folder, which is accessible to the specified supplier. For example,
C:\OneDrive\Prestin. As a result, the files from Folder Path (C:\Supplier 1\Prestin Engineering) will be moved to Destination Path (C:\OneDrive\Prestin). -
Select a suitable label.
-
Select a label from the MPIP Label list based on the level of authorization you want to provide the supplier. For example,
HCAD Confidential. Alternatively, you can select a label with no encryption settings. In this case, you will receive a message "The selected MPIP label has no encryption settings and can only be applied to MIP SDK-supported file types.". If you want to apply such a label, enter the file types that are supported, such as.txt,.docx, and.pdf. -
Alternatively, you can use a custom permission label. Please skip to point 12.
-
-
If you want to give a user full access to the file, i.e. make a user the owner of the file, enter a user email ID in the Owner Email ID. For example,
Designer@halosecude.onmicrosoft.com -
Select Custom Permissions if you want to set the permission now or if the MPIP label has not yet been defined. The author can assign permission to users, groups, or organizations based on the permission level.
-
From the Select Permissions list, select the level of access you want the users to have when you protect the file (Viewer - View Only / Reviewer - View, Edit / Co-Author - View, Edit, Copy, Print / Co-Owner - All Permissions / Only for me). To know the usage rights of the permissions, please refer to the section "Permissions Level and Usage Rights".
-
Specify the users who should have permission to access your file in Enter Users, Groups or Organizations. Type their full email address, a group email address, or a domain name from the organization for all users in that organization separated by comma or space or semicolon. For example
partner@halosecude.com;prestin-support@prestin.com;prestin-techcad@prestin.com -
You can specify how long the labeled file can be accessed in the Expire access field. Use the Never option if you want the label to never expire and to have unlimited access to the file. It can be used for less sensitive content. Alternatively, for highly sensitive content, select a date on the calendar so that recipients other than the owner cannot access the file after the expiry date.
-
-
Click Add Supplier and then click Restart Service. Repeat the previous steps to add more suppliers.
-
Results:
-
You will see a confirmation message after the supplier has been successfully added.
-
The name of the supplier will be added to the list on the left pane.
-
The supplier detail can be viewed on the right pane by clicking the supplier name node.
-
You will see a confirmation message after successfully restarting the service.
-
-
Related tasks:
-
To remove a supplier from the list, click Remove Supplier.
-
If you make changes to the configuration, click Update Supplier to make the changes take effect.
-
Remember to restart the HaloSHARE after making changes.
-
You can find license and service information in the log
C:\Users\UserName\AppData\Local\Secude\HaloSHARE\log.
-
What happens to unconfigured file types?
Any files that are not specified in the HaloSHARE settings should be shared with caution. If you have configured Move to Destination Path, these files will be moved to the destination folder unprotected. Users must therefore be aware of this type of file sharing.
How to Relabel a File or Modify the Applied Label
A designer may need to relabel files in the supplier folder for a variety of reasons, and in some cases, they may decide to remove protection. To accomplish this purpose, HaloSHARE provides the option to remove protection and relabel features by setting the registry key enable_relabeling=on.
-
Files encrypted with MPIP label can be relabeled with Custom Permissions, and vice versa for files encrypted with Custom Permissions.
-
Files encrypted with Custom Permissions can be decrypted using the Remove Protection label.
Prerequisites:
-
Make sure you are the owner of the document, a user with superuser privileges, or a user with export permissions assigned to an already applied label.
-
Make sure that the API permission for relabeling has been configured in the application. For more information, refer to the section “Additional Permission (Only for Relabeling)”.
-
Enable the relabel feature by changing the registry key
enable_relabelingfromofftoon. For more information, please refer to the section "Registry Settings".
Follow the procedure to relabel.
-
Double-click on the
HaloSHAREConfiguration.exefile. -
On the HaloSHARE Configuration screen, change the label as needed. Please note that applying the Remove Protection label will remove protection.
-
Click Update Supplier and then click Restart Service.
Results:
-
Relabeling: The files in the supplier folder will be updated with the new label.
-
Removing protection: The files in the supplier folder will be successfully decrypted.
-
Service Configuration using Admin Tool
After installing the HaloSHARE, you may want to change the configuration. To do so, run the tool ...\Secude\HaloSHARE\hsadm.exe to view the commands. Please note that the admin tool does not support uppercase.
How to update MPIP labels in HaloSHARE?
If a MPIP label is added, removed, or updated in the Microsoft Purview portal, the administrator should restart the HaloSHARE Service so that the changes will take effect.
When is it necessary to restart the HaloSHARE service?
Whenever you modify the HaloSHARE registry settings, then you need to restart the HaloSHARE Service.
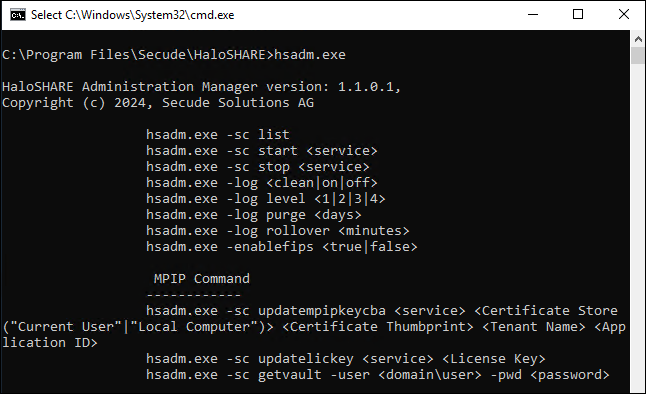
hsadm.exe commands
|
Service Control Commands |
|
Use this command to view the service. Output For a Domain User
For a Non-Domain local user:
|
|
Use this command to start the HaloSHARE. Note: This can be used only after setting user credentials to run HaloSHARE. For example,
Output
|
|
Use this command to stop the HaloSHARE. For example,
Output
|
|
Log Command |
|
For example,
Output
|
|
For example,
Output
|
|
Use this command to set a time for log purging, i.e., the no. of day(s) by which the logs will be deleted. For example,
Output
|
|
Use this command to set a log rollover time, i.e., the minute(s) by which a new log file will be generated. For example,
Output
|
|
MPIP Commands |
|
Update MPIP Certificate
Use this command to update the new MPIP CBA (Certificate-Based Authentication) Keys. For example,
Output
|
|
Update MPIP License Key
Use this command to update the License Key For example,
Output Spring License Key updated successfully |
|
Display MPIP key
Use this command to know your MPIP key information. For example,
Output
|
|
Use this command to enable/disable the FIPS mode. For example,
Output
|
Help Commands
Registry Settings
The following section explains how the registry is used to store service settings. To modify the registry value, open Registry Editor, navigate to this path Registry Root Directory = HKEY_LOCAL_MACHINE\SOFTWARE\Secude\HaloSHARE, and modify the Reg Key as you wanted. Any changes to the registry will require a restart of the HaloSHARE to take effect.
|
Name |
Default value |
Type |
Description |
|---|---|---|---|
|
dir_common |
|
REG_SZ |
The path to the directory where all the dependent DLL files are stored for the execution of HaloSHARE. |
|
dir_log |
|
REG_SZ |
Log files are generated in the service running user's local profile i.e., in the following location |
|
dir_tmp |
|
REG_SZ |
It stores the temporary files located at |
|
dir_vendor |
|
REG_SZ |
This is the Secude’s vendor directory under which Secude’s components will get installed. For example, |
|
enable_fips |
|
REG_SZ |
|
|
enable_relabeling |
|
REG_SZ |
Defines the status of the relabeling.
|
|
haloshare_config_file |
|
REG_SZ |
Name of the configuration file that includes information about the folders and other essential parameters. |
|
log_enable |
|
REG_SZ |
Defines the status of the log.
|
|
log_level |
|
REG_SZ |
|
|
log_purge |
|
REG_SZ |
It indicates removing files older than a defined time frame. By default, the log files older than 7 days will be deleted. |
|
log_rollover |
|
REG_SZ |
Defines the log rollover time, i.e., a new log file will be generated based on the specified minute(s). By default, a new log file will be generated every 100 minutes. |
|
ls_proxy |
|
REG_SZ |
Allows you to use a proxy server to access Secude’s License Manager. This is an optional feature that must be utilized only if your firewall is blocking License Manager. Enter proxy server settings in the format Please make sure to restart the service. |
|
scan_wait_time |
|
REG_SZ |
It indicates the service's waiting time and begins scanning after 5 seconds if the folder has not been modified. |
|
templatefile_purge |
|
REG_SZ |
Defines the purge time of template files that are generated for every CAD assembly file (compound file) download. The default value set is one hour. For example, when a file is downloaded at 15:25 hours, the HaloSHARE service creates a template file in the tmp\GUID folder (which can be located in the HaloSHARE service user's profile folder). In the background, it examines and deletes the files which had reached the configured time i.e., after 16:25 hours. Note: This is only applicable in the event of CAD assembly file labeling. |
|
version |
|
REG_SZ |
The version number of the installed service. |
Configuration in the Registry
Configuring Endpoint
Registry path of endpoint = HKEY_LOCAL_MACHINE\SOFTWARE\Secude\HaloSHARE\ep\HaloSHARE
|
Name |
Default value |
Type |
Description |
|---|---|---|---|
|
block_pii |
|
REG_SZ |
Enable or disable the visibility of Personally Identifiable Information (PII) in the MIP SDK logs. The MIP SDK logs are located at
|
|
cachetype |
|
REG_SZ |
MPIP cache storage type used by the service.
|
|
cacheuserlicense |
|
REG_SZ |
|
|
cloudtype |
|
REG_SZ |
User's Azure Cloud Type. For example: Commercial. |
|
credential |
|
REG_SZ |
Domain or computer name \ name of the user under which HaloSHARE service runs |
|
databoundary |
Default |
REG_SZ |
Audit and telemetry events are sent to the nearest collector, where these events are stored and processed. Other options:
For example, if your AIP administrator sets North_America, the HaloSHARE service forces all telemetry and audit data to go directly to North America. |
|
domain |
|
REG_SZ |
Name of the domain. |
|
enabledke |
0 |
REG_SZ |
Double Key Encryption
Please be aware that DKE labels are only visible when DKE functionality is enabled. |
|
enablefiletracking |
0 |
REG_SZ |
Obtain the protected file's content ID in order to track the file.
|
|
IterationLimit |
10 |
REG_SZ |
Iteration limit for Creo file types. The default value is 10, however you can modify and set your limit. Example: |
|
MIPAuthType |
MSALCBA |
REG_SZ |
Type of authentication method (MSALCBA). |
|
mode |
MPIP |
REG_SZ |
MPIP |
|
policycloudurl |
|
REG_SZ |
Policy Cloud URL. For example: |
|
protectioncloudurl |
|
REG_SZ |
Protection Cloud URL. For example: |
|
service |
|
REG_SZ |
Name of the service. By default, it is HaloSHARE. |
|
streambuffersize |
|
REG_SZ |
It is a buffer size used for memory-based encryption with the MIP SDK. When the allotted buffer size is exceeded, an additional memory of stream buffer size is allocated, and this process is repeated until the encryption/decryption operation is completed. The default setting is 10MB. |
Configuring Endpoint
How to Access Protected Files
After setting HaloSHARE in your environment, you may start sharing business files in folders. Once the files have been protected, you should know how to open MPIP-protected files with HaloCAD Add-ons. Please look in the respective manuals to learn more about how HaloCAD add-ons work.
