This section provides supplemental information.
Open-source Software
Third-party software/code is included or bundled with Secude's products according to its appropriate license. Secude conducts testing to make sure the third-party products are compatible with and perform as intended with Secude applications.
The third-party libraries and dependencies used by HaloSHARE are shown in the table below.
|
Library |
Version |
Source Code |
License Link |
|---|---|---|---|
|
Boost Library |
1.85.0 |
https://boostorg.jfrog.io/artifactory/main/release/1.79.0/source/ |
|
|
Protobuf Library |
5.26.1 |
https://github.com/protocolbuffers/protobuf/releases/tag/v21.2 |
https://github.com/protocolbuffers/protobuf/blob/master/LICENSE |
|
WTL |
9.0 |
||
|
Rapidxml |
1.13 |
https://sourceforge.net/projects/rapidxml/files/latest/download |
|
|
MIP SDK |
1.15.94 |
https://learn.microsoft.com/en-us/information-protection/develop/version-release-history |
https://docs.microsoft.com/en-us/information-protection/develop/ |
|
Licensespring |
7.32 |
- |
- |
|
OpenSSL |
3.2 |
||
|
MSAL |
4.61.3 |
https://github.com/AzureAD/microsoft-authentication-library-for-dotnet |
https://github.com/AzureAD/microsoft-authentication-library-for-dotnet/blob/master/LICENSE |
Open-source software
Permissions Level and Usage Rights
Basic Permissions
The following table lists the basic permissions and the usage rights that they contain:
|
S.No |
Permission Level |
Usage Rights (Allowed Recipient Actions) |
|---|---|---|
|
1 |
View |
Open and read the data (also known as “Read-only”). It includes Zoom and view from different angles (for CAD file types). |
|
2 |
Edit |
Edit the file and save it |
|
3 |
Copy |
Extract data (including screen captures) from the file into the same or another file. |
|
4 |
|
Print the content |
|
5 |
Export |
Save the content to a different filename (Save As). Also includes “Export to PDF”. |
|
6 |
Change Rights |
Changing the label that is applied to a file includes removing protection and saving it as an unprotected file. |
|
7 |
Owner (Full Control rights) |
Grants all rights to the file and all available actions can be performed. And includes the permissions below:
|
Basic Permissions
Author (creator) of a file
The author of a file has all rights and actions mentioned in the above table. Also includes the below permissions:
-
Open file after the expiry date
-
Revoke access
Custom Permissions
The following table lists the custom permissions and the usage rights that they contain:
|
S.No |
Permission Level |
Usage Rights (Allowed Recipient Actions) |
|---|---|---|
|
1 |
Viewer |
Open and read the data (also known as “Read-only”). It includes Zoom and view from different angles. |
|
2 |
Reviewer |
Viewer’s allowed permissions plus:
|
|
3 |
Co-Author |
Reviewer’s allowed permissions plus:
|
|
4 |
Co-Owner |
Co-Author’s allowed permissions plus:
|
|
5 |
Only for me |
Grants all rights to the file and all available actions can be performed only by the author of the file. |
Custom Permissions
Uninstallation
When you no longer use the service, you may uninstall the application. Uninstalling removes all files and registry settings that were added to your computer during the initial installation.
-
Click Start menu > go to Control Panel > Programs > Programs and Features > Uninstall a Program > select HaloSHARE from the list > right-click and select Uninstall option.
-
Depending on your Windows security settings, you may get a security warning as "Do you want to allow the following program to make changes to this computer?". If you get this security warning, click the Yes button to confirm that you want to uninstall the application.
-
The following confirmation message will appear.
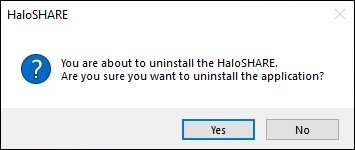
Uninstall message #1
-
Click Yes to confirm that you want to remove it from the computer.
-
The service is uninstalled successfully. Click OK to close the dialog.
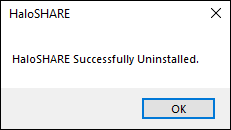
Uninstall message #2
