Introduction
Secude's HaloSHARE is a best-of-breed solution that monitors the configured local or network folders within the organization. HaloSHARE monitors only the folder that the user defines within it. When a file is placed in the configured folder, HaloSHARE encrypts it by effortlessly applying Microsoft Purview Information Protection (MPIP) labels, providing persistent access controls regardless of where it is moved.
What distinguishes HaloSHARE?
In a multiuser environment, where multiple users share access to a system or network, there are several potential file access and security issues. Here are a few common issues:
-
Users may maliciously or unintentionally access other users' files.
-
There is a risk in a shared environment that one user will overwrite or modify files belonging to another user.
-
Inadequate access control systems might let users access files for which they don't have the right authorization.
-
Unauthorized users gain access to sensitive files.
HaloSHARE, a labeling solution, can easily overcome the challenge by encrypting the files without user intervention with a simple drag-and-drop into a specific local folder on a HaloSHARE-installed machine. This means that any file moved within the HaloSHARE's radius (configured folder) is encrypted and protected from accidental file sharing and unauthorized access. As a result, this labeling solution protects your data as it travels within and outside of your organization.
Implementing this solution in your environment reduces the risk of a data breach and guarantees data protection regulations are always followed without the need for security personnel to perform any additional manual procedures.
About this Manual
This guide will walk you through the installation, configuration, and workflow of HaloSHARE.
Features
-
Supports folder-based bulk file protection.
-
Supports both MPIP-based label protection and user-defined custom permissions.
-
Support for easily removing protection as needed and relabeling an already-existing label on a protected file.
-
It supports a variety of CAD file types, as well as PDF and Office files.
General FAQs
This section provides answers to the most frequently asked questions (FAQ). If you have any further inquiries, please get in touch with our sales representative or our support team.
-
What does HaloSHARE provide for an organization?
This labeling solution protects your files and enforces security throughout their full life cycle. -
Does it protect all native Computer-Aided Design (CAD) file types?
Yes, HaloSHARE supports all CAD native file types. -
What happens if an unauthorized person attempts to open a HaloSHARE-labeled file?
At first, user authentication takes place. It is a process of verifying the identity of the user. If the user fails during the authentication, he/she will be prompted with an error message and access will be denied. -
Who decides what labels should be used for various supplier folders and how it is managed in the background?
In an organization, a MPIP administrator is responsible for creating and managing labels (user rights) in the Microsoft Purview portal. The choice of label can be made by engineers or designers who create drawings for a specific supplier. -
What if I don't want a certain file type to be protected?
HaloSHARE encrypts any file based on the extension specified in the configuration. As a result, you can whitelist file types to be encrypted and blacklist file types by not defining them in configuration. -
Is it possible to apply custom permissions to protect a file?
Yes, HaloSHARE allows users to apply custom permissions without using Azure labels. -
How to open a protected CAD file?
You can view a Protected CAD file using a HaloCAD Add-on for CAD applications.
-
How to open a protected PDF file?
You can view a Protected PDF file using the Acrobat Reader DC / Acrobat DC application. Additionally, it can be viewed with the Microsoft Purview Information Protection unified labeling client.
Quick Start Installation Summary
The following image shows the high-level idea of setting up HaloSHARE.
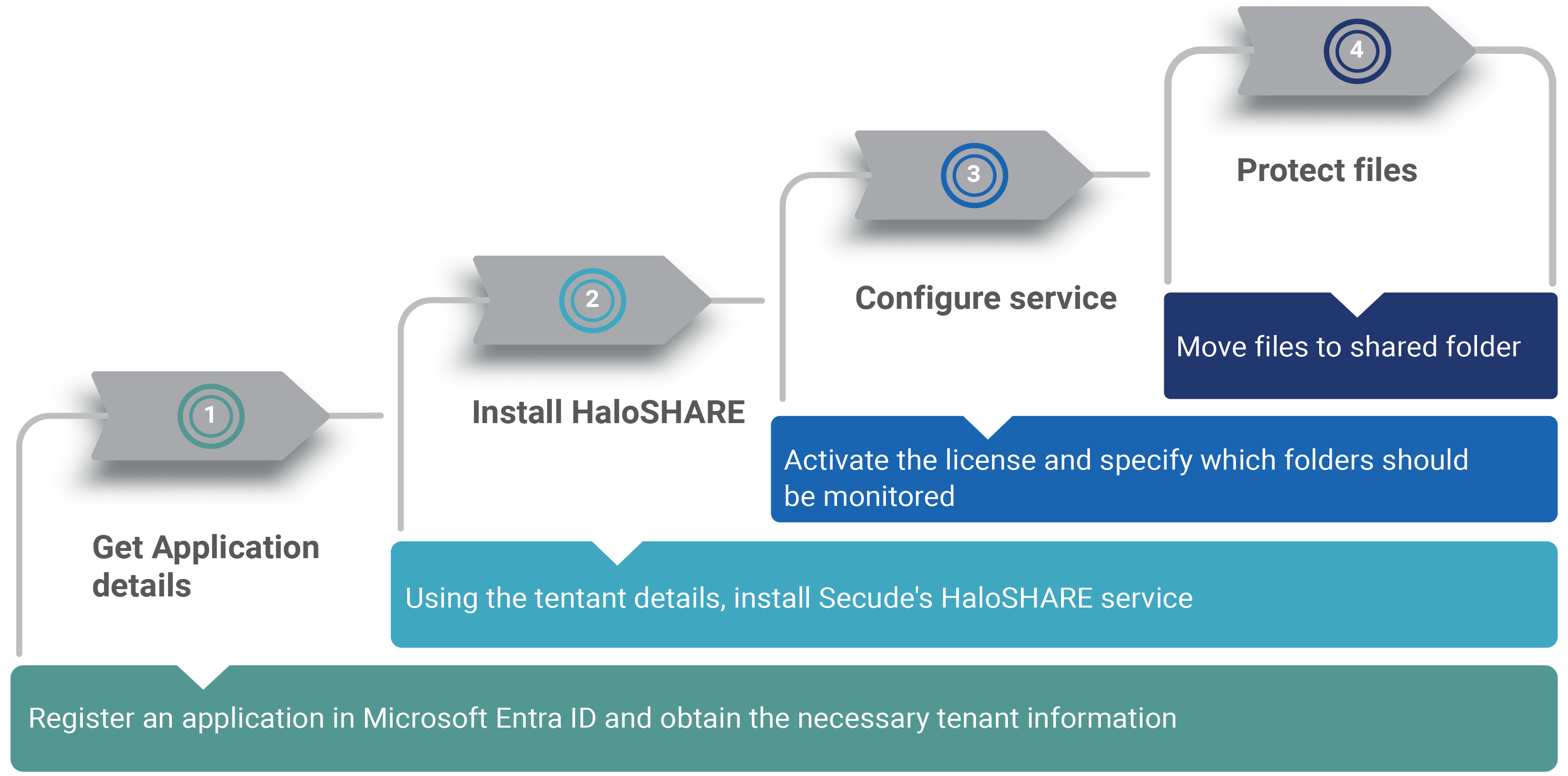
Quick start implementation steps
Architecture
HaloSHARE is a service that runs on a Windows Server that communicates with the Microsoft Rights Management Service (RMS) to encrypt files in a specific folder using predefined MPIP labels or user-defined custom permissions. When any unprotected design files are placed inside the shared folder that HaloSHARE constantly monitors, the files are screened and automatically protected without user intervention based on how the configuration is defined in the service.
Note: When a CAD file is protected by HaloSHARE and shared with partners/suppliers, they can view the file by installing the HaloCAD Add-on for CAD applications on their machines.
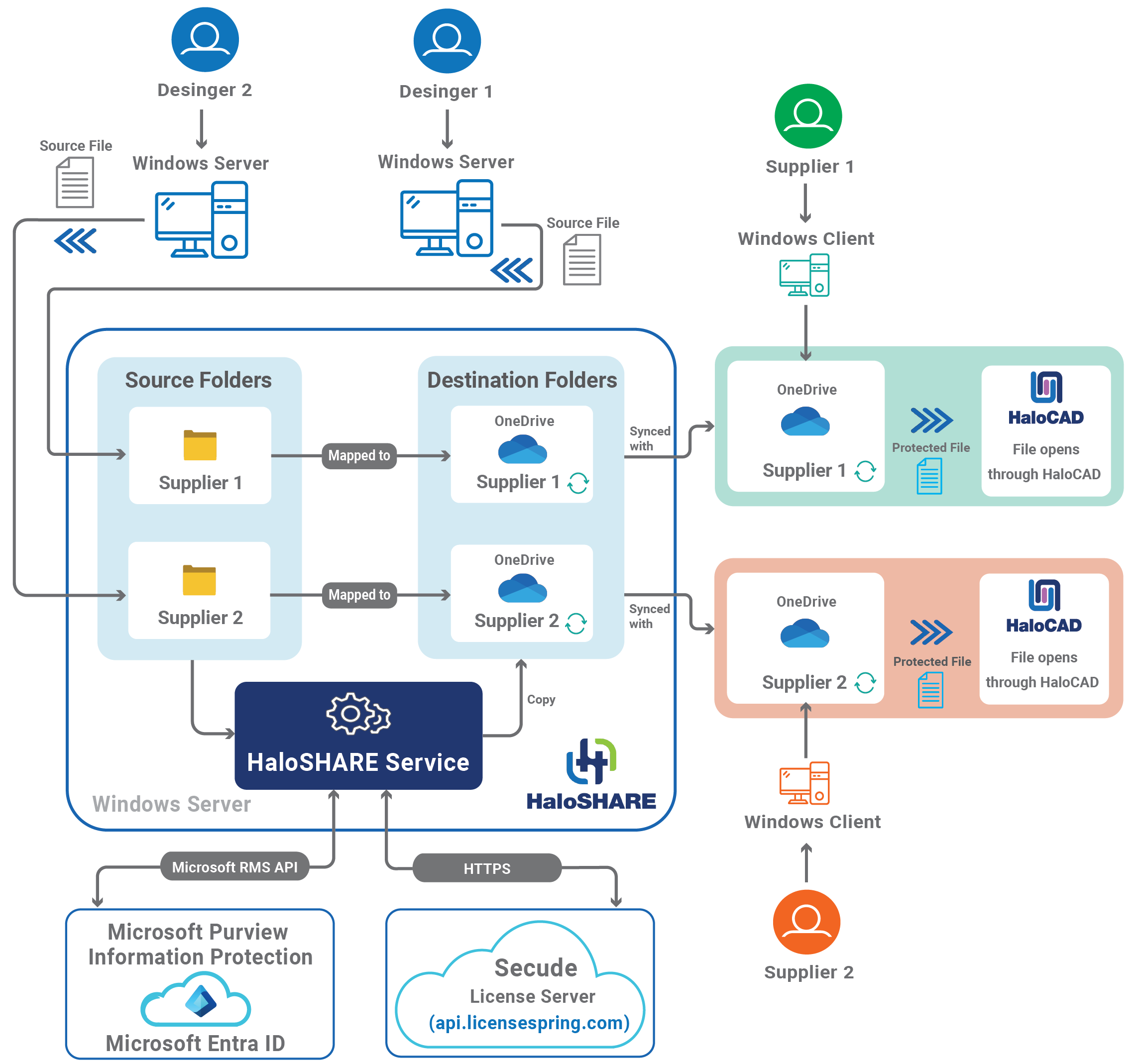
Architecture
At a high level, the HaloSHARE workflow consists of these steps:
-
In an enterprise landscape, different teams create and share files with specific names such as "supplier 1-Prestin Engineering" and "supplier 1-United Engineering" in a locally shared folder on a HaloSHARE-installed machine.
-
HaloSHARE scans the folder and subfolders for new file arrivals determines whether to encrypt or not, and then applies the appropriate MPIP label or custom permission.
-
If HaloSHARE is configured to move a file to a destination folder, the labeled file is copied to the destination location, which is typically a shared folder for your specific supplier, after applying the encryption. The destination folder can be a OneDrive directory. As a result, each supplier gets its own destination folder for sharing business information. In contrast, if moving the file to the destination folder is not enabled, the protected files remain in the source folder.
-
Third parties, such as suppliers, vendors, or external consultants, can only access their folders and consume MPIP-labeled files through HaloCAD Add-ons. Please refer to HaloCAD manuals for more information.
Microsoft documentation
This manual assumes that you already have a complete setup of Microsoft Purview Information Protection and you are familiar with using the Azure portal and related concepts. If you are new to Azure, you can refer to Microsoft online documentation regarding setup and configuration.
System Requirements
The following system requirements table specifies the minimum and recommended technical specifications, such as software and network resources, necessary to run the product.
|
Components |
Details |
|---|---|
|
Operating System |
|
|
Office 365 Subscription |
|
Requirements
Recommended URLs, Addresses, and Ports for MPIP
MIP SDK doesn't support the use of authenticated proxies. So, make sure you set the Microsoft 365 service endpoints to bypass the proxy. View a list of endpoints at Microsoft Online Documentation. However, Microsoft recommends the following:
|
Addresses |
Ports |
|---|---|
|
|
TCP 443 |
|
|
TCP 443 |
|
For event logging
|
TCP 443 |
|
National Cloud |
Microsoft Entra ID authentication endpoint |
|
Microsoft Entra ID for the US Government |
|
|
Microsoft Entra ID (global service) |
|
Recommended endpoints
Secude License Manager
To communicate with Secude License Manager, the following URL and port must be whitelisted in the customer's proxy:
|
Address |
Port |
|---|---|
|
License API - api.licensespring.com |
TCP 443 |
Recommended license manager endpoint
