Prerequisite: Make sure that you have configured the required details as described in the section "Settings in Azure Portal".
For user authentication and validation, you need to register the domain details as instructed below:
-
On the left navigation bar, click Customer Configuration, and then from the Customers list, select one of them.
-
On the Tenant Configuration tab, click Configure.
-
Click the plus icon, and the User Domain-Tenant Configuration page will appear as shown in the figure below:
Note: The values displayed on the example screen are altered for security reasons.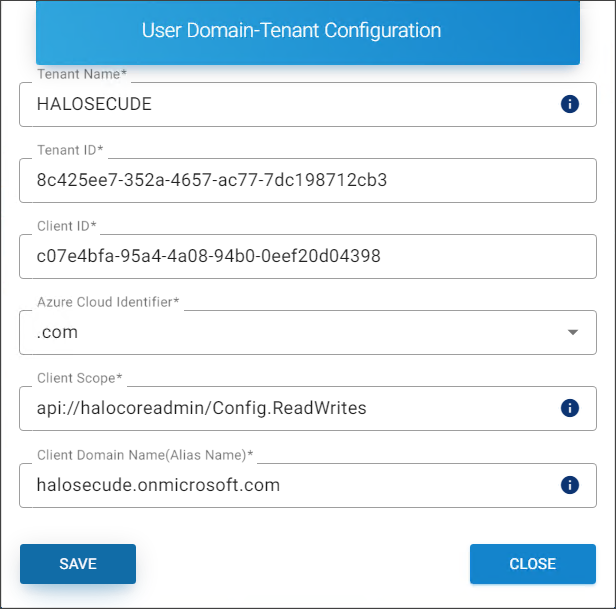
Registering a domain page
-
Tenant Name − Enter the name of your Microsoft Entra tenant. Note: Maximum 30 characters, alphanumeric characters, hyphen, and underscore are only allowed. For example,
HALOSECUDE -
Tenant ID − Enter the unique identifier of your Microsoft Entra ID instance. For example,
8c425ee7-352a-4657-ac77-7dc198712cb3 -
Client ID − Enter the identifier that is assigned when registering the application. For example,
c07e4bfa-95a4-4a08-94b0-0eef20d04398 -
Azure Cloud Identifier − Select the identifier from the list. For example:
.com,.us -
Client Scope − Enter the scope assigned to the application. For example,
api://halocoreadmin/Config.ReadWrites -
Client Domain Name (Alias Name) − Enter an alias name for your domain. For example,
halosecude.onmicrosoft.com. -
Click Save and repeat the above steps to register other tenants.
Results: You will receive a confirmation message after successfully registering the user domain.
Related tasks:
-
Using the appropriate icons, you can also edit or delete a tenant.
-
If you want to view the tenant details, click the Tenant Details icon.
-
You can now see the registered tenants listed under the User Domain-Tenant Configuration page.
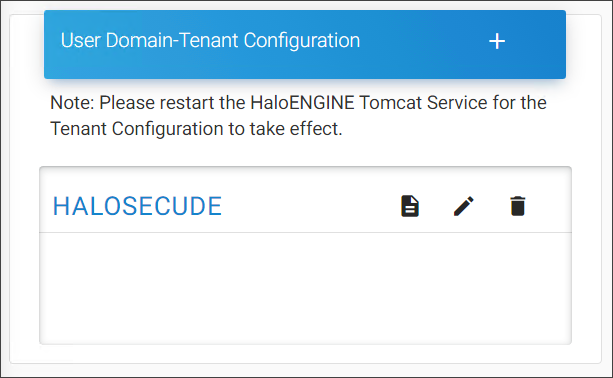
Registered user domain page
What to do next:
-
Restart the HaloENGINE Tomcat service for the configuration change to take effect.
-
Login using the admin account or user account.
User Login (Super Admin / Azure Users)
Once tenant configuration is done and reload is completed, the page will be redirected to the login page. You can select either one of the following options to log in to the portal.
Option 1 − Default Super Admin Account
Option 2 − Microsoft account (log in using user account - Customer_Admin or Customer_User)
-
Click on the button Continue with Microsoft.
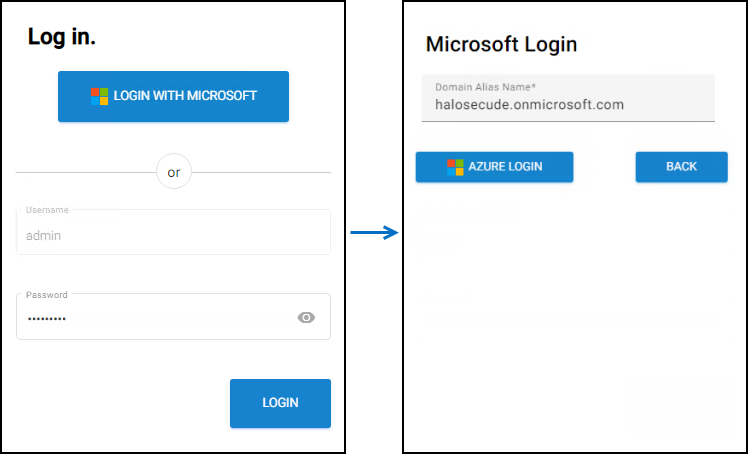
Microsoft Azure Login #1
-
Enter the alias name that is entered in the HaloENGINE Admin Portal and click Azure Login.
-
Microsoft Sign-In Assistant requests you to enter the user credentials.
-
Enter your Azure credentials and click Sign-in.
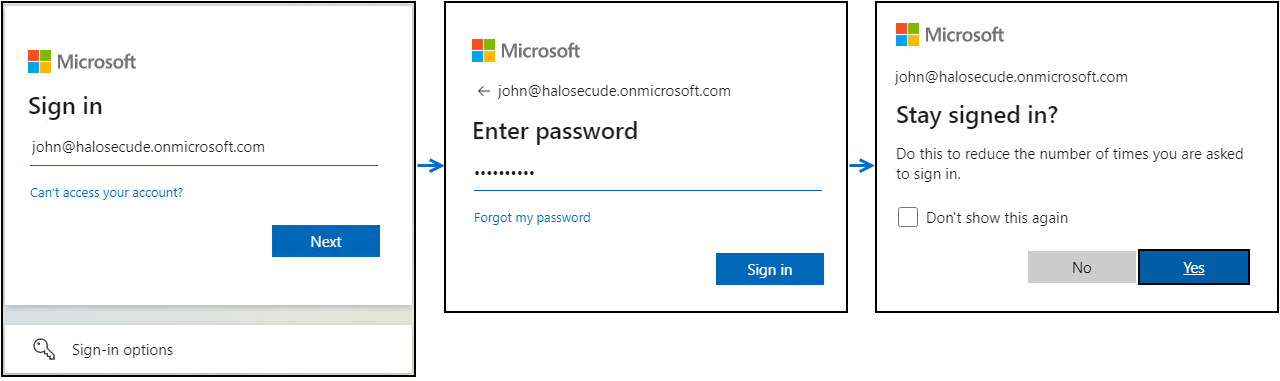
Microsoft Azure Login #2
-
To the question “Stay signed in?" click No/Yes based on your need.
-
After the successful authentication, you will be logged into the portal. Please note that if a user logs into the HaloENGINE Admin Portal using the Azure user account, the access token issued remains valid for a period. Therefore, even if you close the browser, and re-open it or refresh the page, you do not need to enter the credentials again to sign in. However, to enforce the user login, the user must first sign out from the Azure portal.
-
For illustration purposes, user accounts are shown in the below images:
Admin account
User account
Methods to log in admin portal
-
If you are using the Remote Desktop Protocol (RDP) to connect to your HaloENGINE system and log into the Admin Portal, you need to use the default admin account.
-
Alternatively, if you have enabled “Configure Remote Access” you could sign in via the Microsoft Sign option and with the default admin account. Use the following URL:
-
http://<ip>:<port>/haloengine-admin/ui/app/login -
For example,
https://10.41.14.69:8746/haloengine-admin/ui/app/login
-
