This page will help you through the most common problems that may arise during the installation and configuration of the HaloENGINE and Service, which are described below.
HaloENGINE
As the first step in troubleshooting, make sure that your HaloENGINE version is up to date. Each release of HaloENGINE adds new features and fixes many problems. Installing the latest version may clear any problems without the need for further troubleshooting.
Forgot your Admin Portal Password
Symptoms
Login fails with the error message "Invalid credentials".
Background
Entered the wrong password to access the HaloENGINE Admin Portal.
Probable Cause
No matter how careful you are, there may be times when you are unable to access the admin portal because you can't remember your password.
Corrective Action
-
Run Command Prompt as an administrator.
-
Type
haloengine-password-config.bat -hto reset the password. -
Log in with the new password.
Cannot Log in to Microsoft after Configuring the Tenant
Symptoms
The user login fails with the following error message.
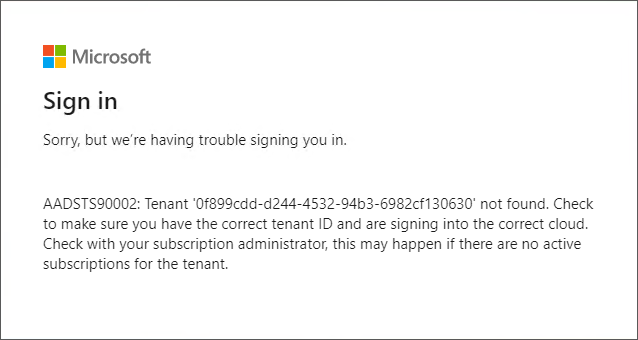
Microsoft Sign-in error message
Background
The above error occurs when a user logs in to a HaloENGINE Admin Portal using Microsoft Sign-In.
Probable Cause
The Tenant ID/Client ID you entered on the User Domain-Tenant Configuration page is either incomplete or incorrect.
Corrective Action
-
Check that the Tenant ID/Client ID given on the User Domain-Tenant Configuration page is correct.
-
Log in to the admin portal.
Unable to Load the Admin Portal—Case 1
Symptoms
One of the following error messages appears in the browser while trying to load the HaloENGINE Admin Portal.
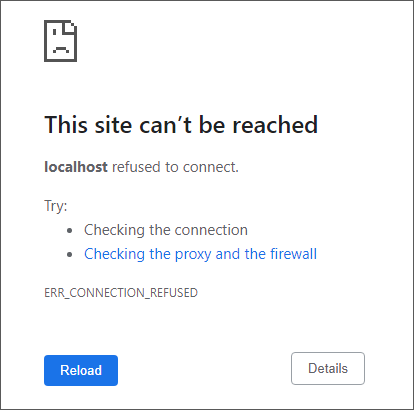
Error message #1
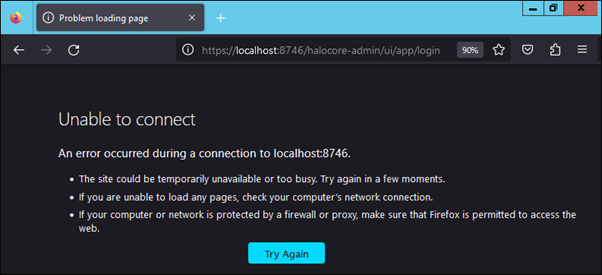
Error message #2
Background
The issue mentioned above happens when a user logs into the Admin Portal after creating the Server Certificate.
Probable Cause
The admin portal loads by default through HTTP on port 8383. However, when a server certificate is generated, the admin portal is forced to load using HTTPS. To load in HTTPS, a client certificate/Root CA must be present in Tomcat's trust store. Failure to generate a client certificate results in an error.
Case 1 (using a self-signed server certificate):
In this case, the self-signed server certificate is created in the HaloENGINE Admin Portal and the HaloENGINE Tomcat service is then restarted without creating a client certificate.
Case 2 (using a signed server certificate):
In this case, Tomcat is restarted after a signed server certificate is installed without importing its Root CA's trust store.
Corrective Action
Case 1 (using a self-signed server certificate):
-
Create a self-signed server certificate.
-
Immediately create a client certificate.
-
Restart the HaloENGINE Tomcat Service.
Case 2 (using a signed server certificate):
-
Import a signed server certificate.
-
Immediately import its Root CA.
-
Restart the HaloENGINE Tomcat Service.
-
Proceed with importing other client certificates.
Unable to Load the Admin Portal—Case 2
Symptoms
Error message #1 occurs in the browser when trying to open the HaloENGINE Admin Portal in the HTTPS protocol.
Background
The above-mentioned message appears when the user deletes the server and client certificates.
Probable Cause
Removing the server certificate permanently removes all other certificates (including client and CA certificates) and causes the admin portal to operate via the HTTP protocol only. This is expected behavior.
Corrective Action
-
Manually change the protocol from HTTPS to HTTP and the port to 8383.
-
Clear your web browser's HTTP Strict Transport Security (HSTS) settings. Please see this link for additional details: How to clear HSTS settings in Chrome and Firefox.
Unable to Load the Admin Portal or PDM Client could not Connect to HaloENGINE
Symptoms
-
Error message #1 occurs in the browser when opening the HaloENGINE Admin Portal.
-
HaloCAD for SOLIDWORKS PDM client cannot connect to HaloENGINE.
Background
The above-mentioned error occurs when the admin portal is attempted to open and the client is unable to connect to the HaloENGINE.
Probable Cause
The HaloENGINE's IP address has been changed after configuration.
Corrective Action
Action 1: Use a static IP address
It is not recommended to change the IP addresses of computers in a large network on a regular basis. Changing HaloENGINE's IP address affects communication with the PDM Client.
Action 2: Update the IP address in hc-servlet.xml
Proactive action: Make sure that FQDN is used to generate the HaloENGINE server certificate instead of the system IP address.
In some circumstances, a strategic change in IP addresses is required due to network restructuring, security incidents, or significant infrastructure upgrades. In this circumstance, follow the below steps:
-
Locate the XML file in
C:/Program Files/Secude/Tomcat/webapps/haloengine-server/WEB-INF/hc-servlet.xml. -
Open the file and adjust the IP address (
publishedEndpointUrl) in the XML file.<jaxws:endpoint id="HaloEngineProcessInterface" implementor="com.secude.haloengine.server.impl.HaloEngineProcessPortImpl" wsdlLocation="WEB-INF/haloengine-server-process.wsdl" address="/process" publishedEndpointUrl = "https://19.41.14.188:8746/haloengine-server/process" /> <jaxws:endpoint id="HaloEngineMonitorEndpoint" implementor="com.secude.haloengine.server.interfaces.audit.HaloEngineServerMonitorPortImpl" wsdlLocation="WEB-INF/haloengine-server-monitor.wsdl" address="/monitor" publishedEndpointUrl = "https://19.41.14.188:8746/haloengine-server/monitor" /> <jaxws:endpoint id="HaloEngineStatefulEndpoint" implementor="com.secude.haloengine.server.interfaces.stateful.HaloEngineStatefulPortImpl" wsdlLocation="WEB-INF/haloengine-stateful-process.wsdl" address="/stateful_process" publishedEndpointUrl = "https://19.41.14.188:8746/haloengine-server/stateful_process" /> -
Save the document.
-
Restart the Tomcat service.
-
Launch the admin portal.
Protection Fails
Symptoms
Protection does not happen, or protection fails.
Background
When a user downloads a file, no protection is applied to the chosen file.
-
For office files, the label is applied, and the file opens unprotected.
-
For non-native files, no label is applied, and an error appears.
Probable Cause
This problem happens when one or more of the following conditions are met:
-
Case 1: If the Classification Engine is turned off.
-
Case 2: If the HaloENGINE Service is not registered and mapped to the current profile.
-
Case 3: If no Action/Classification rules are configured under Download Rules.
-
Case 4: If the HaloENGINE Service/HaloENGINE Tomcat Service stops unexpectedly.
-
Case 5: If the certificate used by the HaloENGINE Service has expired.
-
Case 6: If the System Unique ID on the Admin Portal does not match the System ID on the client system.
-
Case 7 (only for SAP clients):
-
HaloENGINE Server certificate is not imported into STRUST, or it was imported, but is no longer valid or has expired.
-
HaloENGINE (Server) connection is not alive when connected with an SAP instance.
-
If the HaloENGINE Connection Parameters are incorrectly set.
-
Corrective Action
-
Case 1: Check that the Classification Engine is turned on.
-
Case 2: Make sure that a registered HaloENGINE Service is mapped to an appropriate profile (Customer ID).
-
Case 3: Make sure to include an appropriate classification rule, followed by a suitable action rule.
-
Case 4: Check that the HaloENGINE Service is running; if not, restart it manually and then restart the HaloENGINE Tomcat Service. Note: It is recommended to restart the HaloENGINE whenever the HaloENGINE Service is restarted.
-
Case 5: Make sure to upload the same valid certificate that is already installed on the Windows Server machine where the HaloENGINE Service is installed.
-
Case 6: Check that the name entered in the admin portal's System Unique ID field matches the name entered in the System ID (in configuration properties). Also, make sure the names are case-sensitive. Make sure that the client system name matches the name entered in the admin portal's System Unique ID field. Also, make sure the names are case-sensitive. For example, if your client system name is 'MYDESKTOP', but you enter 'mydesktop' in the System Unique ID field, you will receive an error due to case sensitivity.
-
Case 7 (only for SAP clients):
-
If you are using a self-signed certificate, import a valid
HaloENGINEServer.cerinto STRUST. -
Check that the HaloENGINE connection is Alive.
-
On the HaloENGINE Connection Parameters screen, be sure you select the option Activate HaloENGINE and enter the current profile that you are using in Customer ID.
-
-
Re-try downloading now.
Dashboard Fails to Load
Symptom
The dashboard window displays the error message "Failed to get data".
Background
HaloEngine is installed in a custom location with an inbuilt MongoDB option during installation.
After initializing the HaloENGINE admin portal, the Monitor log dashboard fails to load.
Probable Cause
HaloENGINE is installed in the Desktop location path.
Corrective Action
As a best practice, it is not recommended to install it on the HaloENGINE desktop location. However, if you install it on a desktop location, you will encounter this type of error. To resolve it, you need to grant sufficient permission to Network Service.
HaloENGINE Service
As the first step in troubleshooting, make sure that your HaloENGINE Service version is up to date. Each release of HaloENGINE Service adds new features and fixes many problems. Installing the latest version may clear any problems without the need for further troubleshooting.
Installation was Interrupted due to Certificate
Symptom
Error message: "Please check the certificate details and verify the certificate is installed properly.”
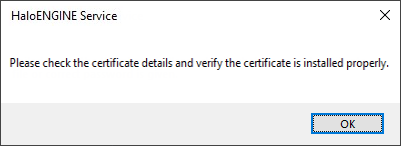
Certificate error message
Background
HaloENGINE Service installation in MPIP results in the error message shown above.
Probable cause
The certificate that you installed in the Certificate Store (Current User or Local Computer) has expired.
Recommended Action
-
Verify the certificate using the Microsoft Management Console (MMC) snap-in.
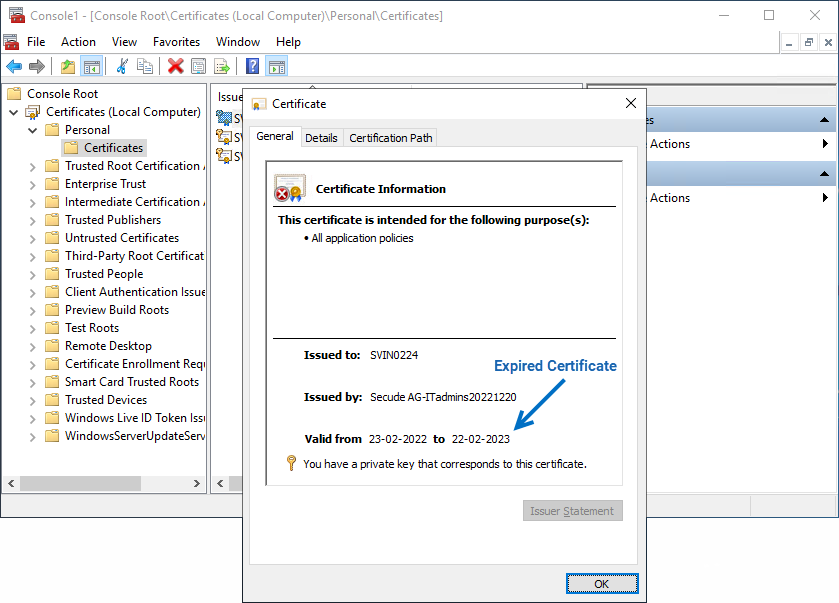
Certificate in MMC
-
If the certificate is invalid, add a new certificate.
-
If you proceed to install HaloENGINE Service at this point, you will receive the following message:
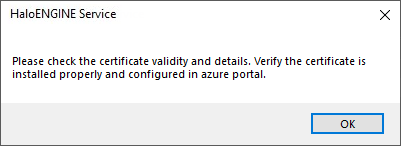
Mismatch of Certificate
-
Make sure that the same certificate is updated on the Azure portal (under the Certificate section > click Upload certificate).
-
Continue with the installation now.
Installation was Interrupted due to Improper Configuration
Symptom
Error message: "Retrieving data for user logon is not possible for this configuration. It might cause problem with service initialization.”
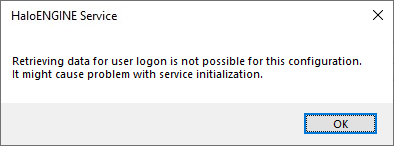
User login / RMS issue
Background
The error message given above appears while installing the HaloENGINE Service.
Probable cause
The username and domain were entered in the improper format.
Recommended Action
-
Enter the user’s name in the proper format.
-
To operate the HaloENGINE Service on a computer that is linked to a domain, you must input a domain user account and password. For example,
[domain]\[user],hc.test\john. -
On a non-domain linked machine, you must input a user's username and password. For example,
.\[user],.\john
-
-
Continue with the installation.
Network Related Issues
Symptom
Case 1
Something bad happened: Failed to send HTTP request with error code 'system:0' Inner exception:
[http_exception:'SSL error: WINHTTP_CALLBACK_STATUS_FLAG_CERT_REV_FAILED failed to check revocation status.'],
NetworkError.Category=Unknown, HttpRequest.SanitizedUrl= https://api.aadrm.com/my/v2/publishinglicenses,
HttpRequest.Id=bbb8ae75-baba-4da5-ae6b-8d1e38d6f7fd, CorrelationId=90a5e1a4-914b-49c5-851f-897aff78ef82,
CorrelationId.Description=ProtectionEngine, CorrelationId=106b4179-e86a-4681-86ef-3bbaa05f9041,
CorrelationId.Description=FileHandler. Exiting
Case 2
"HTTP operation 5928aaf8-7b55-4bcb-bee3-be2a3dde2746 failed: Failed with:
[NetworkError: 'Failed to send HTTP request with error code 'system:0' Inner exception:
[http_exception: 'SSL error: WINHTTP_CALLBACK_STATUS_FLAG_CERT_REV_FAILED failed to
check revocation status. WINHTTP_CALLBACK_STATUS_FLAG_INVALID_CA SSL invalid CA. '],
NetworkError.Category=Unknown, HttpRequest.SanitizedUrl=https://api.aadrm.com/my/v2/
publishinglicenses, HttpRequest.Id=5928aaf8-7b55-4bcb-bee3-be2a3dde2746']"
`anonymous-namespace'::LogHttpOperationDetails
Background
File download/installation fails in MPIP mode, with any of the errors listed in the MIP.log file.
Probable cause
Case 1: Required endpoints stated in (row 125) Microsoft documentation are not permitted in network settings on ports 80 and 443.
Case 2: The problem was caused by an SSL proxy that was configured on the network.
Correct action
Case 1: Verify that both ports 80 and 443 on the network settings are open for the URL listed in row 125.
Case 2: Make sure that the SSL proxy's Root CA is installed on the PC that is running the HaloENGINE Service.
Initialization was Interrupted due to Incorrect Azure Details
Symptom
Error message: "The Tenant ID/name was not found in the Azure directory. Please make sure that you have entered the correct Tenant ID/name/Cloud Type.”
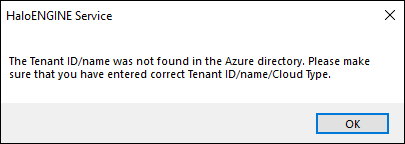
Invalid Azure details
Background
This error message appears during the initialization of the HaloENGINE Service.
Probable cause
The Azure information you provided is inaccurate.
Recommended Action
-
Make sure your Azure tenant ID or name is correct.
-
Choose the suitable cloud type.
-
Continue the installation.
