HaloCORE Monitor
HaloCORE's monitoring solution logs all data download and extraction activity from SAP (GUI and background job) and analytics tools such as SAP BusinessObjects Business Intelligence solutions. HaloCORE's enhanced logging and auditing features give you critical visibility into sensitive data distribution, allowing internal and external audit teams to identify risky areas, users, or transactions. Unlike other auditing solutions, HaloCORE not only records activity but also adds intelligent classification. All extraction activity is aggregated in a fully customizable audit log, which visualizes data downloads based on user, file type, file size, transaction, application, path, terminal, IP address, and classification label. An audit log is a powerful tool that can help you prevent sensitive data loss and lower compliance costs.
Quick Start Implementation | |
SAP System | Windows Server |
|
|
Summarizes the high-level steps to install HaloCORE Monitor
With the HaloCORE monitoring solution, you can also get notified of any users trying to perform the unsanctioned download of compliance-sensitive data. HaloCORE's GRC Extension supplies an enterprise with the ability to get notified regarding risky export behavior. HaloCORE monitors download and data extraction activity in SAP and allows SAP's alerting mechanism to trigger alerts if such actions are performed. As a result, all download and data extraction activity occurring in SAP can be monitored and reported on. Appropriate personnel are made aware of and can acknowledge planned data extraction activity and can investigate unplanned or suspicious activity.
In addition, the audit log can be transferred into other Security Information and Event Management (SIEM) solutions, like Microsoft Azure Sentinel, Splunk, RSA, and others, by creating log files in Common Event Format (CEF), IBM Standard LEEF, and JSON (JavaScript Object Notation).
All download activity is aggregated into a fully customizable audit log, which can be integrated into the company's existing analytics framework and extracted to powerful tools such as SAP Business Intelligence and Analytics solutions.
What is Monitored?
Every download of any data via the SAP GUI and background job is audited. This includes exporting spreadsheets, downloading attachments, and saving data from transactions:
Who performed the download? (user ID and name)
What was downloaded? (file name, size, and file type)
Where from? (transaction code and text, application component, and table name)
Where to? (path, terminal, and IP address)
The solution gives the ability to filter collected entries into configurable groups, for example, by functional area, geographic region, or transaction type. For example, the audit team can analyze download activity around confidential HR information for a specific personnel area or financial reports of a particular legal entity.
Enhanced GRC Functionality
By seamlessly integrating with the existing SAP Access Control infrastructure, HaloCORE's alert mechanism allows organizations to proactively detect security and compliance risks via real-time reporting. HaloCORE monitors all download and data extraction activity in SAP and raises alerts with the GRC mechanism. FireFighter activity review reports are enhanced with additional critical information by including any download activity that occurred during a firefighter session.
The component includes the following features:
FireFighter log enhancement: When a download occurs during a FireFighter session, the HaloCORE Add-On stores this information, within the activity log, in a change document, which is then collected by the FireFighter logging process and displayed by the logging display/alert/mail mechanisms.
Raising of SoD alerts: When a download occurs on a connected SAP NW system, an alert will be sent to the GRC instance. Note: Whether an alert should be raised at all, based on what logic, and what the alert should contain, must be defined in the enhancement spot (/SECUDEGC/ES_ALERT). If "Notification to Risk Owner" is defined, then notification e-mails are sent to the owners of the SoD risk specified in the alert.
Prerequisites
Ensure that the appropriate product package and access to the product documentation are available for the installation.
GRC Extension works together with Data Protection and Data Classification. The HaloCORE Add-On, which is included in either of the main solutions, is required for the GRC extension to function.
Dependency on HaloCORE Log Mode
The integration with GRC functionality is dependent on the HaloCORE log and it is triggered when the log is written to the database: on systems that do not physically store the HaloCORE log (set as "Remote"), GRC integration is not possible. Therefore, you should plan your GRC integration together with the logging, and ideally use log modes "Local" or "Local + Remote". For details, refer to the section "HaloCORE Log Configuration".
Requirements
HaloCORE GRC Server (SECUDEGS) | |
|---|---|
SAP GRC Add-On | GRC Foundation ABAP 10.0 (component GRCFND_A, release V1000) or greater |
HaloCORE GRC Client (SECUDEGC) | |
GRC NetWeaver Plug-In | 10.0 (component GRCPINW, release V1000_700) or greater |
SAP NetWeaver (non-GRC NetWeaver systems) |
|
Requirements
Package Information
The HaloCORE GRC Extension installation package includes .PAT file for GRC (Server) and GRC (Client - non-GRC NetWeaver systems), respectively.
Step 1. Install the GRC Server Add-On
Step 1a: Store the delivery files
Import the .pat files (<product version>\Halocore for GRC (Server)\1_Installation\Data\CN1[…].pat) into the target system's transport directory, in ...\usr\sap\trans\EPS\in. (Depending on the version, either two or four files may be delivered.)
Step 1b: Import the Add-On packages
With transaction SAINT, import the packages:
Logon to client 000 with a user having SAP_ALL authorizations (but not with DDIC or SAP*).
In the menu option click Installation Package > Load Packages > from Application Server, add the packages to the import queue.
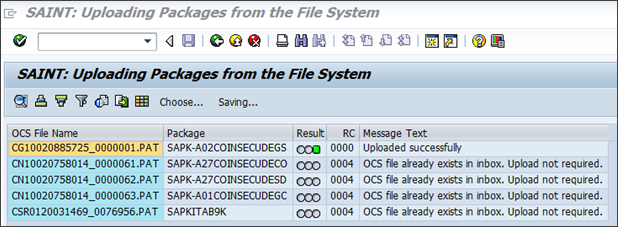
Uploading server installation packages
Click Back or press F3 to go back to the main screen.
Press Start to view your package queue. You can see a package named SECUDEGS.

Installing the GRC Server component
Select the Add-On and click Continue.
To the question "Do you want to add Modification Adjustment Transports to the queue?", answer No.
You may choose to run the import in dialog or the background. (The import process may run for 30 minutes or longer, depending on various factors.)
Click the Finish button.
Step 2. Install the GRC Client (non-GRC NetWeaver systems) Add-On
Step 2a: Store the delivery files
Import the .pat files (<product version>\HaloCORE for GRC (Client)\1_Installation\Data\CN1[…].pat) into the target system's transport directory, in ...\usr\sap\trans\EPS\in. (Depending on the version, either two or four files may be delivered.)
Step 2b: Import the Add-On packages
With transaction SAINT, import the packages:
Log on to client 000 with a user having SAP_ALL authorizations (but not with DDIC or SAP*).
In the menu option click Installation Package > Load Packages > from Application Server, add the packages to the import queue.
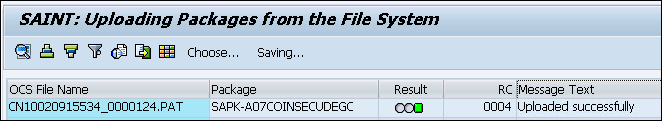
Uploading client installation packages
Click Back or press F3 to go back to the main screen.
Press Start to view your package queue. You can see a package named SECUDEGC.
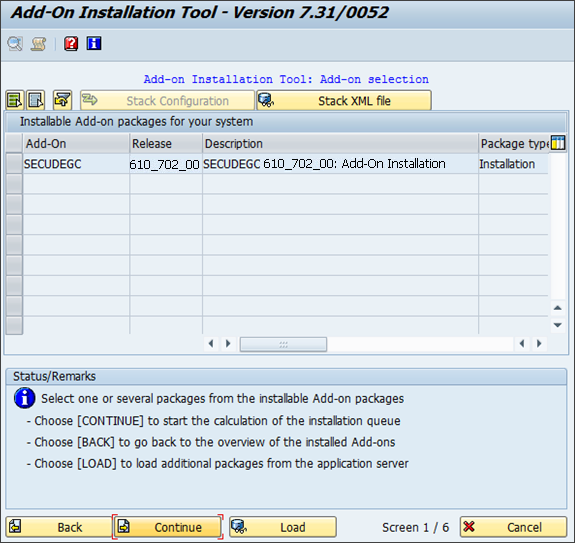
Installing the GRC Client component
Select the Add-On and click Continue.
To the question "Do you want to add Modification Adjustment Transports to the queue?", answer No.
You may choose to run the import in dialog or background. (The import process may run for 30 minutes or longer, depending on various factors.)
Click the Finish button.
Step 3. HaloCORE for GRC Configuration
Call the transaction /n/SECUDEGC/PARAMS to configure the HaloCORE Add-On with GRC.

HaloCORE for GRC Configuration
Select GRC Integr. Active check box, to integrate the HaloCORE SAP Add-On with GRC.
Specify the RFC destination of a connected GRC instance in the RFC Destination GRC box. Note: This parameter is optional. If not set, the configuration of the GRC plug-in (parameter ID 1001) is read.
Specify the RFC destination of this system for access from a connected GRC instance in OWN RFC Destination box. Note: This parameter is optional. If not set, the configuration of the GRC plug-in (parameter ID 1000) is read.
Select Write Change Docs option to enable the HaloCORE Log to be additionally written in the form of change documents. This allows a connected SAP GRC instance to retrieve the log for display, e.g., as part of a FireFighter session.
Select Only f. FireFighters option, if you want the change documents to be created only for users who have the FireFighter role assigned to them. If this option is not selected, the change documents are written for all users.
To select this option, the Write Change Docs option must also be enabled.
Select Raise Alerts option if you want to send risk alerts from the HaloCORE Add-On.
Click Save to save the changes.
Restricted Content
Some sections of our documentation portal are exclusively available to licensed customers. If you are a licensed user, please log in to https://tech.secude.com to continue.
Operations
This section explains the process of viewing HaloCORE's activity log entries inside the FireFighter log and how to raise Alerts generated via the HaloCORE Add-On.
Viewing the FireFighter Log Report
When a download occurs through FireFighter ID, the HaloCORE download log will be additionally written into the Change Documents of the FireFighter user.
Prerequisite: The option Write Change Docs must be enabled in HaloCORE for GRC configuration.
Login to NWBC.
The My Home page appears.
Select Reports and Analytics tab and click Consolidated Log Report.
Select Change Log in Report Name list and view the report.
The Consolidated Log Report displays HaloCORE download details with default components.
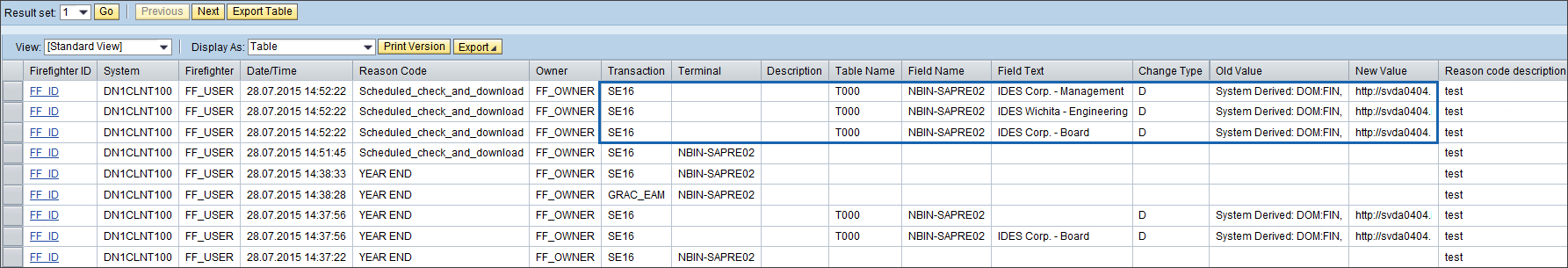
Default HaloCORE download log components in FireFighter Log
The column New Value displays the URL of the HaloCORE log. Clicking the New Value will take you to a detailed list of the selected data.
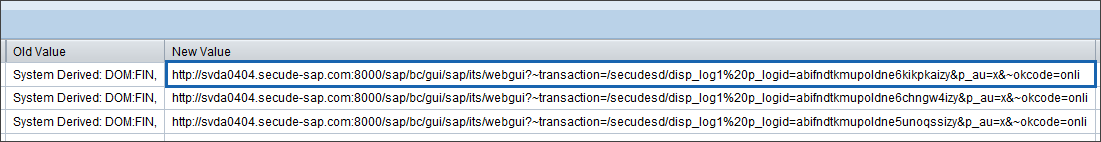
New Value with URL
Viewing the SoD Risk Alerts
This section describes how to view the Risk Alert details. When a download occurs through FireFighter ID, an alert will be sent to the GRC. Based on the implemented enhancement spot, notification e-mails are sent to the owners of the SoD risk specified in the alert.
Prerequisite: The option Raise Alerts must be enabled in HaloCORE for GRC configuration.
Login to NWBC.
The My Home page appears.
Select Access Management tab and click Conflicting and Critical Risk Alerts.
Specify System/Alert Date Time/Date Time Executed/User ID and click Search.
The Risk Alert Details are displayed.
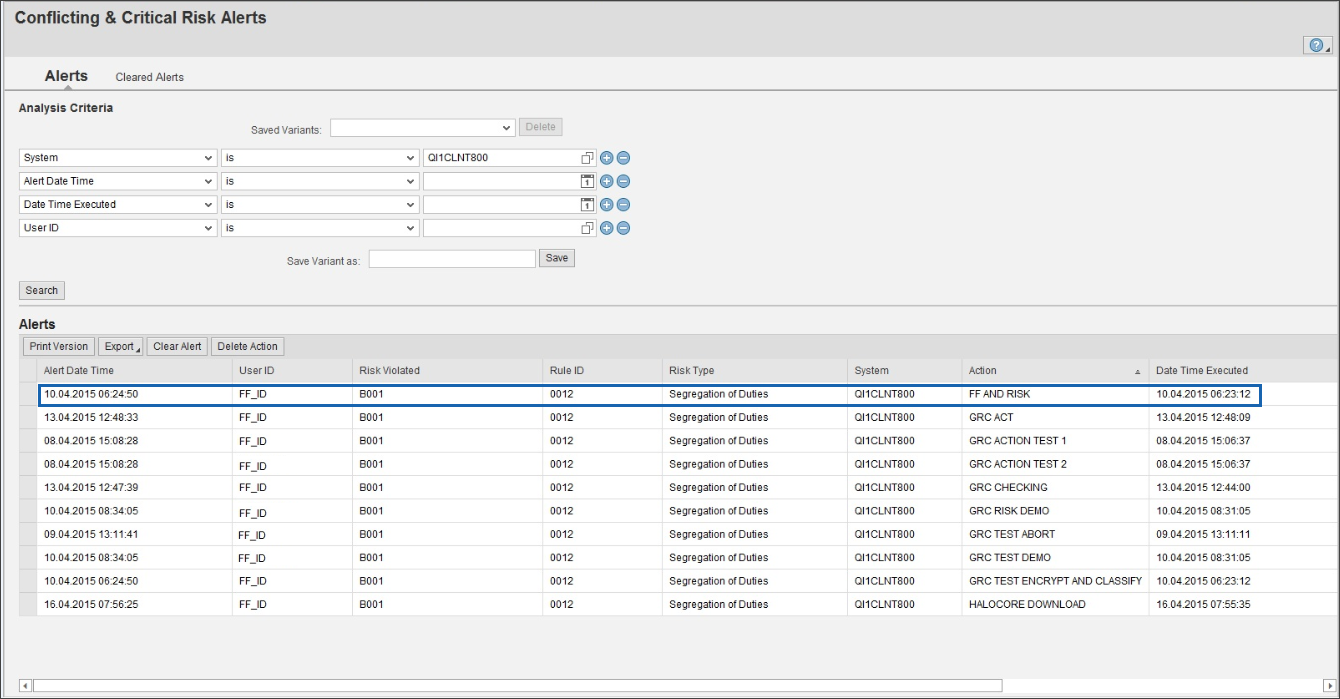
Download Risk Alert details
Uninstalling the GRC Client Add-On
Please refer to the section "Uninstalling HaloCORE GRC Add-on".
SIEM Integration
Every networked environment generates thousands of logs from disparate systems. It is very difficult to detect malicious activity in such a vast landscape. Hence, to gain visibility for SAP-based download activity, HaloCORE allows forwarding logs to Security Information Event Management systems. Before forwarding logs, it is important to format them to a standardized format. HaloCORE supports Common Event Format (CEF), Log Event Extended Format (LEEF), and JavaScript Object Notation (JSON).
Common Event Format is an open log management standard developed by HP ArcSight. CEF comprises a standard prefix and a variable extension that is formatted as key-value pairs.
Log Event Extended Format is a customized event format for IBM Security QRadar. LEEF comprises a LEEF header, event attributes, and an optional Syslog header.
JavaScript Object Notation is a lightweight text-based open standard designed for human-readable data interchange.
Once formatted, the messages are passed over to the communications module that handles the transmission of the messages to your collecting server using the UDP or TCP protocol. Ideally, you would want the SIEM (Microsoft Azure Sentinel, Splunk, RSA, and others) server to read the messages that are received, sort them, and send out alarms to your security team.
To know about the log format definition, please refer to the section "Download Log Definition".
