Network Settings
This section explains the required network settings and communication between each component.
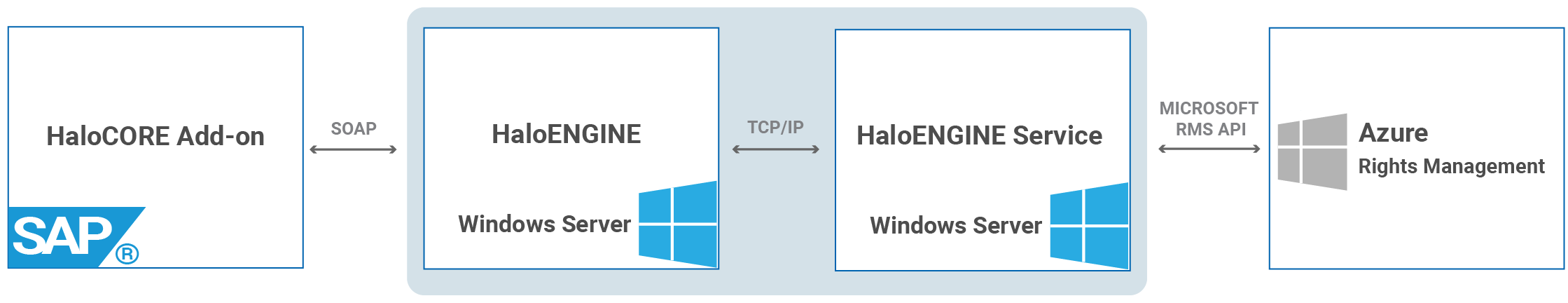
Network settings
Check Server Connectivity: Your SAP server must be able to communicate with the server on which you want to install the HaloENGINE.
Once the HaloENGINE is configured, make sure to install
HaloENGINEServer.cerin STRUST and SAP instance certificate in HaloENGINE. For more details, please refer to the section "Importing the HaloENGINE Certificate into ABAP System".The HTTPS [port 8746] protocol is used for the connection between SAP NetWeaver and HaloENGINE. Through this connection, the SAP Add-On, passes the raw attributes mined from the ABAP context to the HaloENGINE and sends the data to be protected, and receives the protected data.
The TCP/IP (default port 20000) protocol is used for the connection between HaloENGINE and HaloENGINE Service.
HaloENGINE Service communicates with Microsoft Purview Information Protection (MPIP) to obtain the labels and then protects the file with the appropriate label.
SSCR Key: As part of the HaloCORE SAP Add-On installation, we must modify SAP sources in an SAP system. For example, to modify the function module GUI_DOWNLOAD and its subroutines, you must register the function group on the SAP Service Marketplace (object key R3TR FUGR SFES) and, of course, you need to have a developer key and suitable authorizations. Check for allowed system changes in the target SAP client (SCC4).
Activate Web Dynpro for ABAP: If Web Dynpro on SAP is not activated, please follow the instructions in the section "Activating Web Dynpro in SAP".
Azure RMS: Activated Azure RMS and working Microsoft Entra ID service must be available, including user accounts assigned with appropriate RMS rights. For more details about configuring Azure RMS, please refer to the official documentation available from Microsoft.
Ensure the functionality and status of the Azure Rights Management Services before the installation of HaloCORE.
Use Office 365 or 2013 and Azure RMS-enabled users to protect some content with the service to ensure its functionality.
Within a typical cloud environment, the following certificates will be used:
Baltimore CyberTrust Root (to access login.windows.net or graph.windows.net for Graph API queries).
Microsoft Root Certificate Authority 2011 (to access your
LicensingIntranetDistributionPointUrlfor example, can be obtained by using PScmdlet Get-AadrmConfiguration).
Create and configure sensitivity labels and their policies in the Microsoft Purview portal.
