Installation Manual
Introduction
HaloCAD KPro is a Java-based component that is a proxy for HaloCORE for DMS Add-On and communicates with the HaloENGINE and HaloENGINE Service.
About this Manual
This manual walks you through installing and configuring HaloCAD KPro and includes many references to other sources of related information.
System Requirements
The following table lists the requirements for HaloCAD KPro.
Required components | Details |
|---|---|
The following components are necessary for a DMS-integrated environment.
|
|
For an ECTR integrated environment with CAD application, HaloCAD for CAD application, as well as the components listed above, are necessary. | Please refer to the HaloCAD Installation Manual for more information on how to set up the add-on. |
Requirements
Installing the HaloCAD KPro Application
Setting up HaloCAD KPro involves installing the HaloCAD KPro application (which installs Tomcat, Java, and deploys the KPro war file) and adjusting the war properties via the command line.
Note:
If HaloCAD KPro is running on the same computer as the HaloENGINE, the HaloCAD KPro installer will use Tomcat and Java, which have already been set up by the HaloENGINE Server installer.
If HaloCAD KPro is installed on a different machine, Java and Tomcat will be installed by the HaloCAD KPro installer.
Tomcat must be restarted following any configuration or Tomcat certificate configuration.
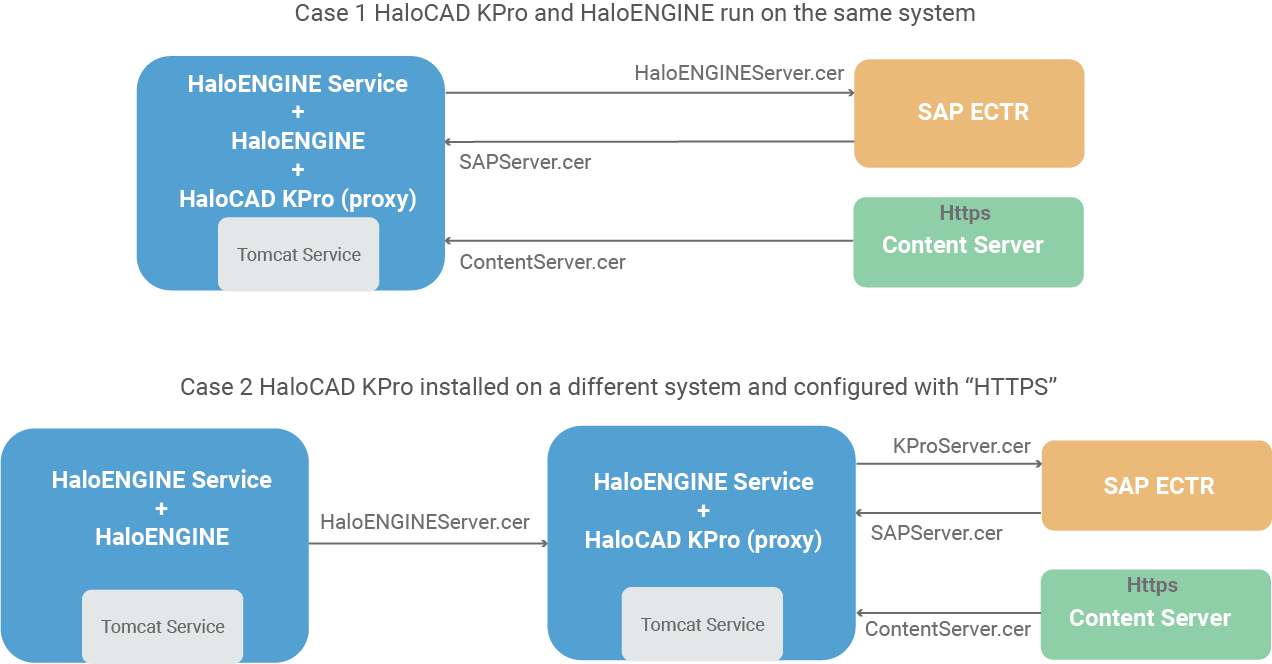
HaloCAD KPro installed in different setups
Install the HaloCAD KPro using the GUI-based setup program provided in the installation package.
To begin the interactive installation, double-click the installer
HaloCAD_KPro_Setup.exefile. Depending on your Windows security settings, you may get a warning such as "Do you want to allow the following program to make changes to this computer?". If you get this security warning, click the Yes button to continue the installation.When the installer starts, you will see the startup dialog followed by the welcome dialog:

Startup Dialog
Welcome dialog
Click Next to continue the installation. The end-user license agreement dialog will appear:
End-User License Agreement dialog
Read the End-User License Agreement. If you agree, select I accept the terms in the License Agreement and click Next.
The Tomcat memory pool size configuration dialog will appear:
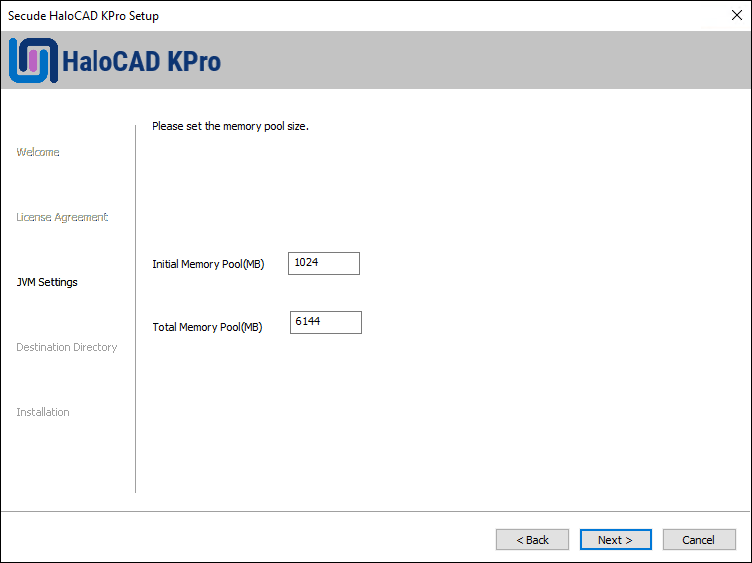
Tomcat pool size configuration dialog
If you want to change the default values of the Initial Memory Pool and Total Memory Pool, enter the amount of memory you want to allocate. Note: Make sure that the Total Memory Pool should not exceed the available RAM on the System. Click Next.
The destination folder selection dialog will appear:
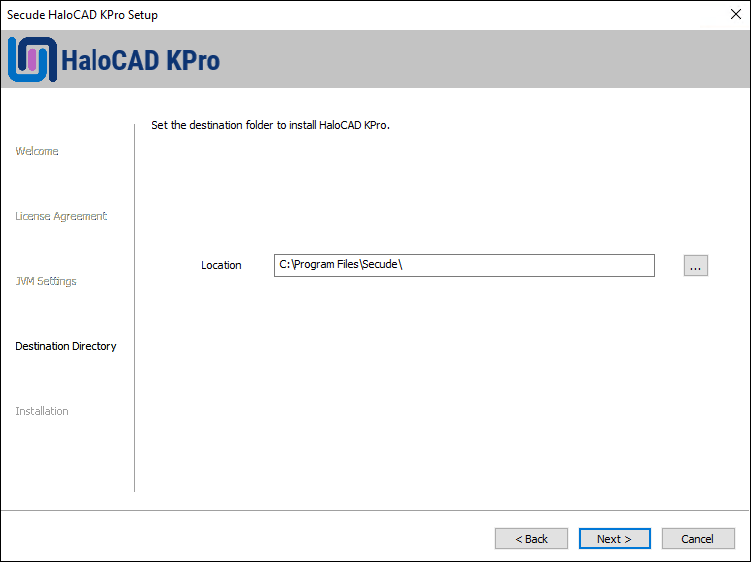
Destination folder dialog
By default, application files are stored in the program files directory (
C:\Program Files\Secude\). If you would like to choose an alternate location, click the Browse button and select your location preference. When you are finished, click Next.The installation begins and progress is shown in the dialog.
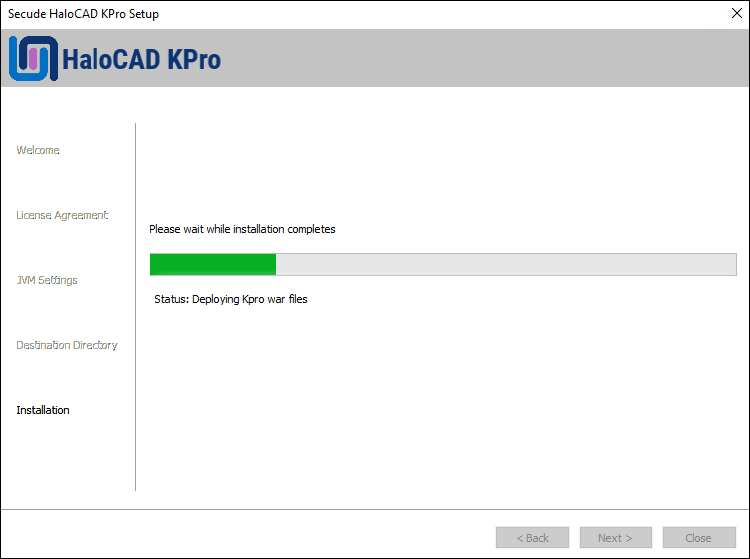
Installing dialog
When the installation is completed, you will see a message confirming that the HaloCAD KPro has been successfully installed.
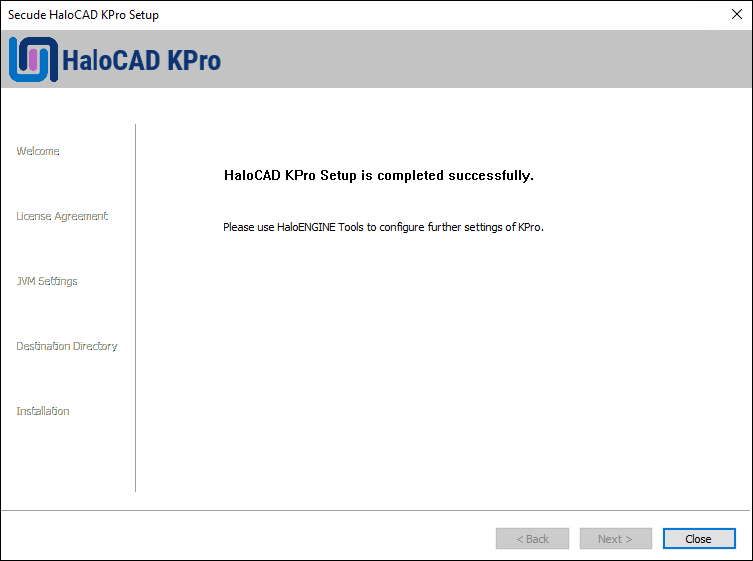
Completing the HaloCAD KPro dialog
Click Close to close the installation wizard.
What to do Next?
Configure HaloCAD KPro using the HaloENGINE Tool.
Silent Installation
Besides graphical mode, the HaloENGINE can be installed in silent mode, which does not require user involvement or display a user interface. Open a command prompt, navigate to the installer's folder, and enter HaloCAD_KPro_Setup.exe -help. Enter the required input and press Enter. The installation will be completed successfully.
Configuring the KPro Properties
Case 1: HaloCAD KPro and HaloENGINE on the Same Machine
Prerequisites
At this point, the HaloENGINE must be able to fetch MPIP labels.
The Server Keystore and a Client Keystore for KPro Proxy must be available in the HaloENGINE. For illustration purposes, the Client Keystore (for example,
ClientKey.jks) is used for communication between HaloCAD KPro and HaloENGINE.For HTTPS Content Server only:
Please note that HaloCAD KPro defaults to HTTPS = False.
To use HTTPS, you need to get the Content Server instance certificate and then add it to the Keystore (HaloENGINE Tomcat) using the HaloENGINE tool.
To allow a failover mechanism, ensure that both HaloENGINEs (primary and secondary) use the same configuration profiles and rules). Thus, if the primary HaloENGINE fails, the secondary HaloENGINE automatically takes over, ensuring uninterrupted operation.
Follow the steps to set up HaloCAD KPro:
Step 1: Set the Environment Variable.
Under System Variables, set the variable
JAVA_HOMEto the Secude JRE directory. For example,JAVA_HOME=C:\Program Files\Secude\secude-jre.Under System Variables, edit the
Pathvariable to addJAVA_HOMEto it. For example,Path=%PATH%;%JAVA_HOME%\bin.
Step 2: Generate KPro configuration properties.
Extract the zipped folder.
To run the HaloENGINE tools:
Copy
halo-engine-tools<version>.zipfile to the desktop and extract it.Open Command Prompt with administrator rights and change directory to
halo-engine-tools-<version>\bin.Run the options one by one. For illustration purposes, a sample is given below.
Syntax, " or " Output
|
Select 1 to proceed with case 1.
|
Option 1 Description: Creates HaloCAD KPro configuration properties. |
Select 1 from the output list.
|
Option 2 Description: Make changes to the war file. |
Select 2 from the output list.
|
Option 3 Description: Make changes to |
Select 3 from the output list.
|
Option 4 Description: Make changes to “MaxThreads” in |
Select 4 from the output list.
|
Option 5 Description (only for HTTPS-enabled Content Server): If your Content Server is HTTPS-enabled, you must use this option to add the Content Server certificate to the HaloENGINE Tomcat Keystore. |
Select 5 from the output list.
|
Option 0 Description: Once you have finished the above instructions, press entering option 0 to leave the command line. |
Case 2: HaloCAD KPro and HaloENGINE on a Different Machine
Prerequisites: Make sure the following files are present on the machine with HaloCAD KPro installed:
Set the Environment Variable as described in step 1.
Client Keystore (
.jks) and HaloENGINE certificate (HaloENGINEServer.cer).Configuration file
HaloENGINE-admin-config.zip. Whenever the admin configuration is changed,HaloENGINE-admin-config.zipshould be imported again with the tool.SAP client certificate
Content Server certificate
Certificate Authority certificate
To allow a failover mechanism, ensure that both HaloENGINEs (primary and secondary) use the same configuration profiles and rules). Thus, if the primary HaloENGINE fails, the secondary HaloENGINE automatically takes over, ensuring uninterrupted operation.
Follow the steps below to set up HaloCAD KPro for Case 2.
Syntax, " or " Output
|
|
Option 1 Description: Creates HaloCAD KPro configuration properties. |
Select 1 from the output list.
|
Option 2 Description: Make changes to the war file. Please note that the redirecting port will only appear when KPro is installed in HTTP mode, and will not appear in HTTPS mode. |
Select 2 from the output list.
|
Option 3 Description (Optional): If you choose to install KPro as HTTPS, proceed to Option 3. This will create a “serverkeystore” for KPro, which works as the server for clients like SAP. It is advised to configure it as HTTPS for security reasons. |
Select 3 from the output list.
|
Option 4 Description (Optional): If you have a Content server certificate in PFX format, use this option to convert it to a server keystore. |
Select 4 from the output list.
|
Option 5 Description: Imports Certificate Authority certificate into KPro keystore. Perform this step if your certificate has been signed by a CA. |
Select 5 from the output list.
|
Option 6 Description: If you have a CA signed |
Select 6 from the output list.
|
Option 7 Description: Make changes to Tomcat web.xml. |
Select 7 from the output list.
|
Option 8 Description: Make changes to “MaxThreads” in Tomcat server.xml. |
Select 8 from the output list.
|
Option 9 Description: If “https” was enabled in option 3, the HaloENGINE Server certificate ( |
Select 9 from the output list.
|
Option 10 Description: Imports the configuration zip file ( |
Select 10 from the output list.
|
Option 11 Description: Imports client certificates such as SAP system certificate into KPro, which works as the server for the clients. If you have multiple SAP systems, you must import their certifications one by one using this option. |
Select 11 from the output list.
|
Option 12 Description: Imports Content Server signed certificate into KPro, which works as the server for the clients. |
Select 12 from the output list.
|
Option 13 Description (only for HTTPS-enabled Content Server): If your Content Server is HTTPS-enabled, you must use this option to add the Content Server certificate to the HaloENGINE Tomcat Keystore. |
Select 13 from the output list.
|
Option 14 Description: Use this option to delete a client certificate. |
Select 14 from the output list.
|
Option 15 Description: Use this option to remove a CA certificate. |
Select 15 from the output list.
|
Option 16 Description: Use this option to remove the KPro Server certificate from server.xml. Please note that deleting the KPro Server certificate also deletes the server and client certificates permanently. Note: It is not recommended to remove the HTTPs certificate because doing so will obstruct connection between the ECTR Client and the Kpro proxy. However, if you delete the HTTPs KPro Server certificate, be sure to run options 1 and 2 to modify the existing configuration to run protocol HTTP on 8383. |
Select 16 from the output list.
|
Option 17 Description: Use this option to remove CA certificates. |
Select 17 from the output list.
|
Option 18 Description:
|
Select 18 from the output list.
|
Option 0 Description: Once you have finished the above instructions, press entering option 0 to leave the command line. |
Test the Configuration
Restart the HaloENGINE Tomcat service.
Enter the web service endpoint in a browser:
<http(s)://<IPaddress or FQDN>:<port>/halocad-kpro/new-service?wsdl>.For example,http://10.41.14.69:8383/halocad-kpro/new-service?wsdlThe endpoint must be resolved with no error.
HaloCAD KPro Schedulers
Schedulers perform basic duties to systematically handle setup, run in the background, and improve operational efficiency.
Auto Clearance of Session Files
HaloCAD KPro comprises two Schedulers to delete old files based on file expiration criteria. As a default behavior during a file upload/download, a folder is created with a unique session ID. When the session ends, a JSON file will be created in Tomcat's temp directory, which contains session details.
For example: [{"expiration":"yyyymmddhhmmss","sessionId":"ebabc39a-5c10-478b-b61c-9e292ce1fe9b"}]
Scheduler ECTR—Here, the actual expiry for a session is calculated from 3 hours after the session ID's end session function is triggered. Thus, the files are maintained in the same folder and remain valid for another 3 hours. However, the scheduler runs (
sessiondetails.json) every 2 hours on session IDs, examines and deletes the files which had reached their expiration.Scheduler KPro—Here, the actual expiry for a session is calculated 1 hour after the session ID's end session function is triggered. The scheduler runs (
kprosessiondetails.json) every 3 hours on session IDs, examines and deletes the files which had reached their expiration.
Scheduler for HaloCAD KPro Log file
Every day at 3 a.m., an automatic scheduler runs in the background and deletes the log files HaloCAD_KPro.log based on the log retention period specified in the kpro_config.properties file. Log files older than the retention period will be deleted. For example, if you specify 10, log files older than 10 days will be deleted. Range: 1 to 90 days.
How to Update?
This section describes how to update HaloCAD KPro from previous versions to the latest version. Please note that HaloCAD KPro 6.7 is only compatible with HaloENGINE 6.7.
Update from HALOCORE KPro to HaloCAD KPro
This section is for users who are using previous versions of HALOCORE KPro (for example, <6.6) and want to update to HaloCAD KPro.
Step 1: Backup files from earlier version of HALOCORE KPro.
Stop the Tomcat Service
Take a backup of the configuration and the Tomcat folders.
Uninstall the HALOCORE KPro version using the installer.
Step 2: Create files that are compatible with the new HaloENGINE.
If the Halo Core Server is installed, please migrate with the appropriate batch file for HaloENGINE compatibility and upgrade to HaloENGINE 6.7.x.x.
At this point, make sure both HaloENGINE Service and HaloENGINE are installed.
Step 3: Run the batch file.
Create a system variable
JAVA_HOMEand copy theHaloENGINE_HOMEvalue. For example,JAVA_HOME = D:\test\SECUDE\secude-jreOpen a command prompt and navigate to the folder where
makeNewKProConfig.batis available in the product package.Execute the batch file as shown below:
CODEmakeNewKProConfig.bat <path to the old config file> <a backup folder name> For example: makeNewKProConfig.bat D:\Office\Test_zip_files\config D:\Office\Test_zip_files\config_backupIf the script (
.bat) is executed without issues, the backup folder will be automatically deleted. Ensure that the backup folder is free of any other files as it will be deleted.The folder that contains the older "config" will be replaced with the new 6.7 compatible "config".
Step 4: Install HaloCAD KPro version
Install HaloCAD KPro using the installer.
Stop the Tomcat service.
Create a
configfolder in the HaloCAD KPro installation folder.Copy the files from the
D:\Office\Test_zip_files\configto theHaloCAD KPro\configfolder.Execute
halo-engine-tools.batto generate the log folder.Start configuring using the tool, as described in Case 1 (1 to 5). Note: To use the previous versions (<6.6) of the server certificate
HalocoreServer.cer, simply rename it toHaloENGINE.cer.
Update of HaloCAD KPro from Version 6.7.x.x to 6.8.x.x
This section is for those who have already installed HaloCAD KPro 6.6 and want to update to the latest 6.7 version. It is recommended to make a backup of the configuration properties file.
Navigate to the directory in which the HaloCAD KPro installation package is located and double-click the HaloCAD_KPro_Setup.exe.
The installation begins with the following dialog:
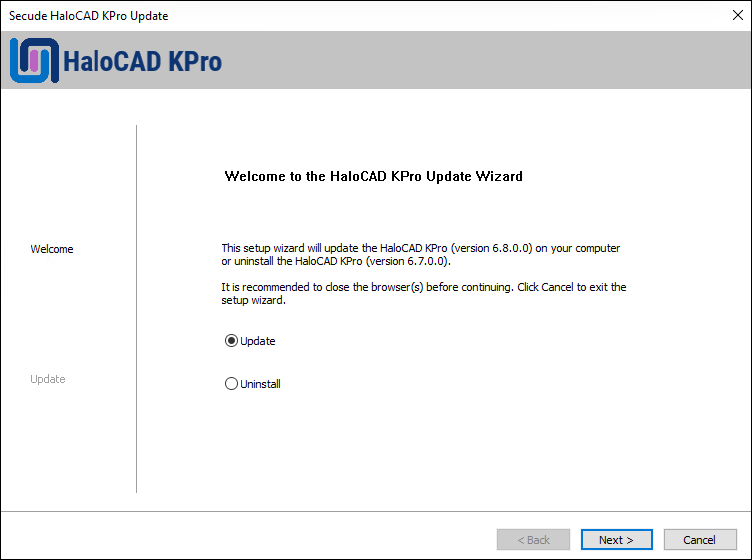
Update screen
If you choose to remove the component, choose Uninstall; otherwise, select Update and proceed to Step 4. To remove, follow the steps outlined below.
Uninstall: If you wish to uninstall the KPro component, select Uninstall and click Next.
To the question, "You are about to uninstall the HaloCAD Kpro. Are you sure you want to uninstall the application?", answer Yes.
To the question, "Do you want to keep the HaloCAD Kpro configuration files?", answer Yes. It is only possible to keep the Tomcat folder, and the only way to obtain the configuration files is to manually create a backup. If you select No, no files will be saved for backup.
After completing the uninstallation process, click Close to close the wizard.
Update: The update will begin, and once finished, you will see the completion dialog.
Click Close to close the update wizard.
Use the HaloENGINE tool to adjust the configuration. Note: To use the previous versions (<6.6) of the server certificate
HalocoreServer.cer, simply rename it toHaloENGINE.cer.
Permission
After completing the configuration, there will be
kpro_config.propertiesfile created atC:\Program Files\Secude\HaloCAD KPro\config.If you don't specify a location for the error log and local audit log, the directory defaults to
C:\Program Files\Secude\HaloCAD KPro\logs\. You must ensure that these directories allow accessing them in your system. To do so, assign folder permissions to "ALL APPLICATION PACKAGES".
Appendix
This section provides supplemental information.
Open-source Software
Third-party software/code is included or bundled with Secude's products according to its appropriate license. Secude conducts testing to make sure the third-party products are compatible with and perform as intended with Secude applications.
The third-party libraries and dependencies used by HaloCAD KPro are shown in the table below.
Library | Version | Source Code | License Name | License Link |
|---|---|---|---|---|
javax.xml.bind:jaxb-api | 2.3.1 | CDDL-1.0 | ||
javax.xml.ws:jaxws-api | 2.3.1 | CDDL-1.0 | ||
javax.xml.soap:javax.xml.soap-api | 1.4.0 | CDDL-1.0 | https://github.com/javaee/javax.xml.soap/blob/master/LICENSE | |
javax.annotation:javax.annotation-api | 1.3.2 | CDDL-1.0 | https://github.com/javaee/javax.xml.soap/blob/master/LICENSE | |
com.sun.activation:javax.activation-api | 1.2.0 | https://repo1.maven.org/maven2/javax/activation/javax.activation-api/1.2.0/ | CDDL-1.0 | https://github.com/javaee/activation/blob/master/LICENSE.txt |
com.sun.activation: jakarta.activation | 1.2.2 | CDDL-1.0 | ||
org.slf4j:slf4j-api | 1.7.36 | MIT | ||
com.sun.xml.bind:jaxb-impl | 2.3.5 | CDDL-1.1 | ||
jakarta.xml.bind:jakarta.xml.bind-api | 2.3.3 | BSD 3 | https://github.com/eclipse-ee4j/jaxb-api/blob/master/LICENSE.md | |
joda-time:joda-time | 2.12.7 | Apache 2.0 | https://github.com/JodaOrg/joda-time/blob/master/LICENSE.txt | |
net.iharder:base64 | 2.3.9 | Public Domain | ||
org.graylog2:syslog4j | 0.9.60 | LGPL 2.1 | https://github.com/graylog-labs/syslog4j-graylog2/blob/master/LICENSE | |
ch.qos.logback:logback-classic | 1.2.14 | LGPL 2.1 | ||
ch.qos.logback:logback-core | 1.2.14 | LGPL 2.1 | ||
com.googlecode.json-simple:json-simple | 1.1.1 | Apache 2.0 | https://github.com/fangyidong/json-simple/blob/master/LICENSE.txt | |
org.apache.commons:commons-lang3 | 3.13 | Apache 2.0 | https://github.com/apache/commons-lang/blob/master/LICENSE.txt | |
nl.basjes.parse.useragent:yauaa | 5.23 | Apache 2.0 | ||
org.eclipse.persistence:org.eclipse.persistence.moxy | 2.7.9 | https://github.com/eclipse-ee4j/eclipselink/tree/master/moxy | EPL 2.0 | https://github.com/eclipse-ee4j/eclipselink/blob/master/LICENSE.md |
com.google.guava:guava | 33.0.0-jre.jar | Apache 2.0 | ||
org.apache.logging.log4j:log4j-api | 2.20.0 | Apache 2.0 | https://github.com/apache/logging-log4j2/blob/release-2.x/LICENSE.txt | |
com.javax0.license3j:license3j | 3.2.0 | Apache 2.0 | ||
javax.servlet:javax.servlet-api | 4.0.1 | CDDL-1.0 | ||
org.apache.poi:poi-ooxml | 5.2.3 | Apache 2.0 | ||
com.univocity:univocity-parsers | 2.9.1 | Apache 2.0 | ||
com.opencsv:opencsv | 5.9 | Apache 2.0 | ||
com.ibm.icu:icu4j | 70.1 | ICU license | ||
com.fasterxml.jackson.core:jackson-databind | 2.18.1 | Apache 2.0 | https://github.com/FasterXML/jackson-databind/blob/2.13/LICENSE | |
com.datastax.oss:java-driver-core | 4.17.0 | Apache 2.0 | ||
com.datastax.oss:java-driver-query-builder | 4.17.0 | Apache 2.0 | ||
com.datastax.oss:java-driver-mapper-runtime | 4.17.0 | Apache 2.0 | ||
org.json:json | 20211205 | org.JSON | ||
org.apache.httpcomponents:httpclient | 4.5.14 | Apache 2.0 | https://github.com/apache/httpcomponents-client/blob/master/LICENSE.txt | |
com.google.protobuf:protobuf-java | 3.21.12 | BSD 3-Clause | https://github.com/protocolbuffers/protobuf/blob/master/LICENSE | |
org.apache.cxf:cxf-rt-frontend-jaxws | 3.5.8 | Apache 2.0 | ||
org.apache.cxf:cxf-rt-rs-security-cors | 3.5.8 | Apache 2.0 | ||
org.apache.cxf:cxf-rt-ws-rm | 3.5.8 | Apache 2.0 | ||
com.sun.xml.ws:rt | 2.3.0 | https://jar-download.com/artifacts/com.sun.xml.ws/rt/2.3.0/source-code | EDL 1.0 | |
org.springframework: spring-context | 5.3.33 | https://github.com/spring-projects/spring-framework/tree/main/spring-context | Apache 2.0 | https://github.com/spring-projects/spring-framework/blob/main/src/docs/dist/license.txt |
org.springframework:spring-web | 5.3.33 | https://github.com/spring-projects/spring-framework/tree/main/spring-web | Apache 2.0 | https://github.com/spring-projects/spring-framework/blob/main/src/docs/dist/license.txt |
org.codehaus.woodstox:stax2-api | 3.1.4 | Apache 2.0 | ||
org.springframework.boot:spring-boot-starter-web | 2.7.18 | Apache 2.0 | https://github.com/spring-projects/spring-boot/blob/main/LICENSE.txt | |
org.springframework.boot:spring-boot-starter-security | 2.7.18 | Apache 2.0 | https://github.com/spring-projects/spring-boot/blob/main/LICENSE.txt | |
org.springframework.security:spring-security-jwt | 1.1.1. | Apache 2.0 | https://github.com/spring-projects/spring-security-oauth/blob/main/license.txt | |
o.jsonwebtoken:jjwt | 0.9.1 | Apache 2.0 | ||
javax.resource:javax.resource-api | 1.7.1 | CDDL-1.0 | https://github.com/javaee/javax.resource/blob/master/LICENSE | |
commons-io:commons-io | 2.5 | Apache 2.0 | https://github.com/apache/commons-io/blob/master/LICENSE.txt | |
commons-fileupload:commons-fileupload | 1.2.1 | Apache 2.0 | https://github.com/apache/commons-fileupload/blob/master/LICENSE.txt | |
commons-beanutils:commons-beanutils | 1.9.4 | Apache 2.0 | https://github.com/apache/commons-beanutils/blob/master/LICENSE.txt | |
org.springframework.boot:spring-boot-gradle-plugin | 2.7.18 | https://github.com/spring-projects/spring-boot/tree/main/spring-boot-project | Apache 2.0 | https://github.com/spring-projects/spring-boot/blob/main/LICENSE.txt |
org.springframework.batch:spring-batch-core | 4.3.10 | Apache 2.0 | https://github.com/spring-projects/spring-batch/blob/main/LICENSE.txt | |
org.springframework.batch:spring-batch-infrastructure | 4.3.7 | Apache 2.0 | https://github.com/spring-projects/spring-batch/blob/main/LICENSE.txt | |
org.springframework.boot:spring-boot-starter-actuator | 2.7.18 | https://github.com/spring-projects/spring-boot/tree/main/spring-boot-project | Apache 2.0 | https://github.com/spring-projects/spring-boot/blob/main/LICENSE.txt |
org.springframework.hateoas:spring-hateoas | 1.4.1 | Apache 2.0 | https://github.com/spring-projects/spring-hateoas/blob/main/LICENSE | |
org.jolokia:jolokia-core | 1.7.2 | Apache 2.0 | ||
org.dizitart:nitrite | 3.2.0 | Apache 2.0 | https://github.com/nitrite/nitrite-java/blob/develop/LICENSE.md | |
com.microsoft.azure:msal4j | 1.7.1 | https://github.com/AzureAD/microsoft-authentication-library-for-java | MIT | https://github.com/AzureAD/microsoft-authentication-library-for-java/blob/dev/LICENSE |
org.springframework.boot:spring-boot-starter-oauth2-resource-server | 5.8.2 | https://github.com/spring-projects/spring-boot/tree/main/spring-boot-project | Apache 2.0 | https://github.com/spring-projects/spring-boot/blob/main/LICENSE.txt |
org.springframework.security:spring-security-oauth2-jose | 5.8.2 | Apache 2.0 | https://github.com/spring-projects/spring-security -https://github.com/spring-projects/spring-security/blob/main/LICENSE.txt | |
org.springframework.security.oauth:spring-security-oauth2 | 2.5.2.RELEASE | Apache 2.0 | https://github.com/spring-projects/spring-security -https://github.com/spring-projects/spring-security/blob/main/LICENSE.txt | |
org.springframework.security:spring-security-oauth2-client | 5.8.2 | Apache 2.0 | https://github.com/spring-projects/spring-security -https://github.com/spring-projects/spring-security/blob/main/LICENSE.txt | |
org.springframework.security.oauth.boot:spring-security-oauth2-autoconfigure | 2.6.8 | Apache 2.0 | https://github.com/spring-projects/spring-security -https://github.com/spring-projects/spring-security/blob/main/LICENSE.txt | |
Tomcat | 9.0.102 | Apache 2.0 | ||
Java | 11 | - |
Open-source software
Uninstalling the HaloCAD KPro Component
When you no longer use the service, you may uninstall the application. Uninstalling removes all files and registry settings that were added to your computer during the initial installation.
Follow the below steps to uninstall:
Click Start menu > go to Control Panel > Programs > Programs and Features > Uninstall a Program > select HaloCAD KPro application from the list > right-click and select Uninstall option or double-click on the installer
HaloCAD_KPro_Setup.exe.Depending on your Windows security settings, you may get a security warning as "Do you want to allow the following program to make changes to this computer?". If you get this security warning, click the Yes button to confirm that you want to uninstall the application.
The following confirmation message will appear:

Uninstall message #1
Click Yes to confirm that you want to remove it from the computer.
You will be prompted to save a backup of the configuration files.
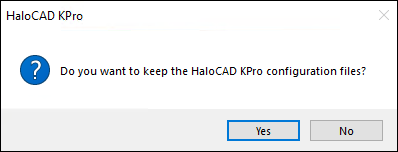
Uninstall message #2
Click Yes. It is only possible to keep the Tomcat folder, and the only way to obtain the configuration files is to manually create a backup. If you select No, no files are taken as a backup.
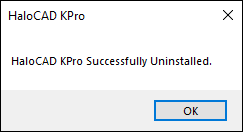
Uninstall message #3
Click OK to close the message.
Customer Support
Please be ready with the information listed below before contacting our team to help you with the issue you are experiencing. The data that you provide will help us serve you better.
Full contact details.
HaloCAD KPro, HaloENGINE, and HaloENGINE Service build version.
Date, time, and description of the error (if possible, provide screenshots).
What (if any) third-party products (software or other) were used in conjunction with our product?
Any other information necessary to reproduce the error.
Secude offers help and support through
Technical support email: support@secude.com
If you choose to contact us by email, please provide your company details and a detailed description of the issue, as well as the log file (if any). Our representative will respond to your email inquiry.Phone support: Call +41 41 510 70 70 to talk to our representative to diagnose and resolve the technical problem.
Other resources
Please visit https://secude.com to know about upcoming events, press releases, and to download whitepapers.
Documentation Feedback
Secude understands the importance of technical content when attempting to gain product knowledge and strives to continuously improve product documentation to ensure that users receive the information they want. To provide feedback on the documentation, please send an email to documentation@secude.com. Please include the following details in your feedback:
Product name and version
Documentation topic
Details of the suggestion or error
The technical documentation team will consider your feedback and address it in future documentation updates.
