Installation Manual
Introduction
To perform business analytics, SAP users extract numerous reports from BusinessObjects BI applications, often containing highly sensitive data. HaloCORE extends its support to monitor, block, classify, and protect the reports containing sensitive information directly from BusinessObjects BI applications (via BO/BI interfaces like WebI and Crystal Reports 20xx/4 Enterprise in Launchpad) by HaloCORE BO Add-On.
HaloCORE BO Architecture
The components of HaloCORE BO are explained in this chapter.
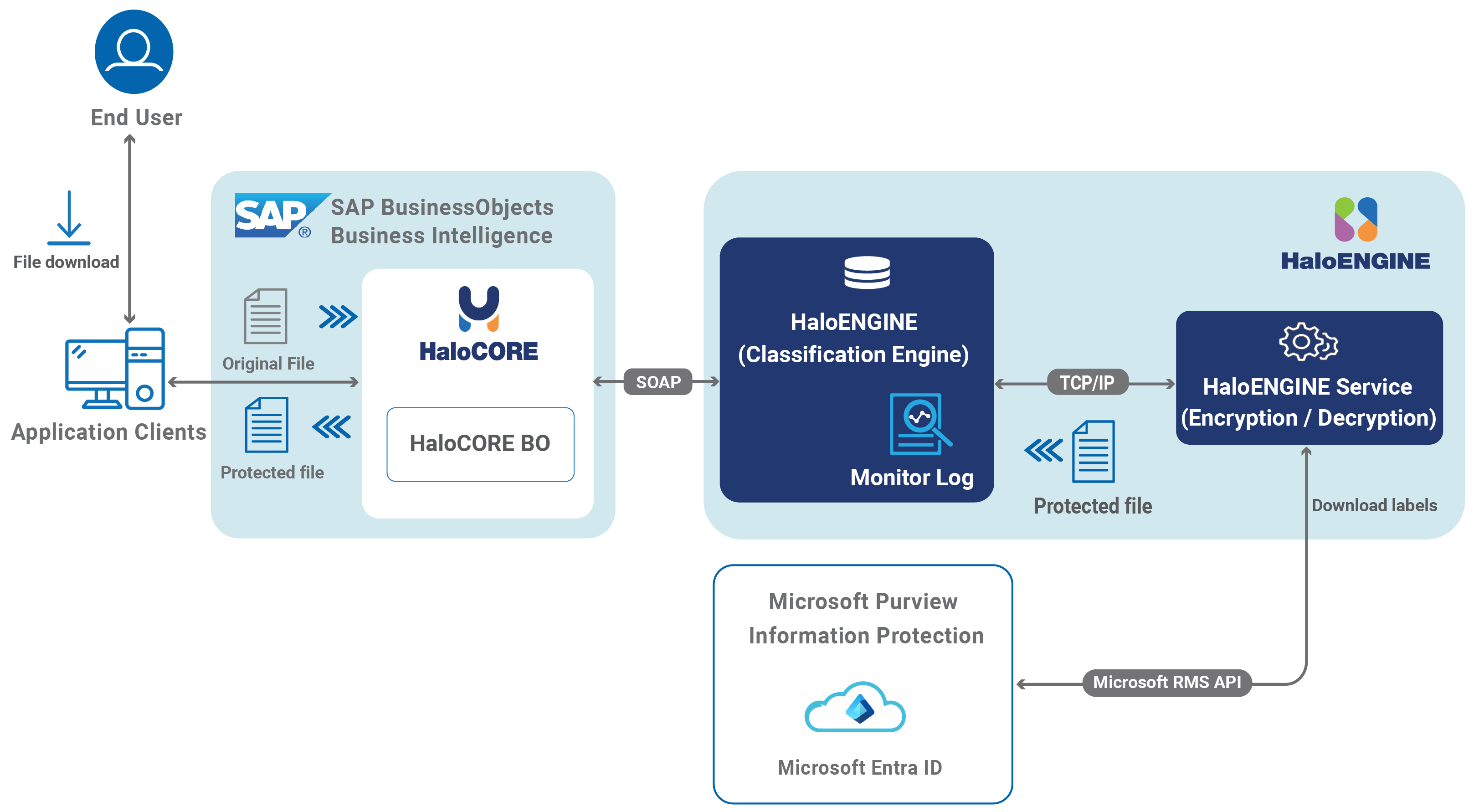
HaloCORE BO Architecture
HaloCORE BO Add-On
HaloCORE BO plugs into BusinessObjects BI applications and intercepts all download requests from users using BO/BI interfaces like WebI and Crystal Reports 20xx/4 Enterprise in Launchpad. Downloaded files are classified and protected. All download activity is aggregated into a fully customizable audit log, which can be integrated into the company's existing analytics framework and extracted to powerful tools such as SAP Business Intelligence and Analytics solutions.
It blocks a file download as defined in HaloENGINE.
Classifies and labels the file as defined in the HaloENGINE.
Encrypts the file as defined in the HaloENGINE.
HaloENGINE
HaloENGINE is a Java-based Server component that exposes a web service to a Non-SAP client such as BusinessObjects BI. It receives files from Non-SAP clients with the passed action and additional information; it applies the action (Monitor, Block, Label, and Protect).
Responsible for classification & action derivation.
Responsible for logging the audit logs.
Create log files for Security Information and Event Management solutions (Microsoft Azure Sentinel, Splunk, RSA, and others) in Common Event Format (CEF), IBM Standard LEEF, and JSON (JavaScript Object Notation).
HaloENGINE Service
HaloENGINE Service is a Windows service that communicates with HaloENGINE over TCP/IP. It is the only component that directly talks with the Azure Right Management Service (Azure RMS).
Applies the classification labels to the document metadata.
Protects the content that the HaloENGINE sends to it based on MPIP.
Supports protection or label-driven protection.
HaloENGINE Service is operated next to the HaloENGINE.
Reference Manuals
Please refer to the manuals shipped with the product software for a comprehensive description of HaloENGINE and HaloENGINE Service.
Microsoft Purview Information Protection
HaloCORE solution effortlessly integrates Microsoft Purview Information Protection to protect your sensitive documents. Microsoft Purview Information Protection is an industry document security solution that enables businesses to ensure that only authorized users can open the protected content while also regulating what they can do with it such as print, edit, or save. Even if sensitive data is leaked accidentally or maliciously, unauthorized parties cannot view it in clear text, thus leaving it useless.
Quick Start Installation Summary
The following image shows the high-level idea of setting up HaloCORE BO.
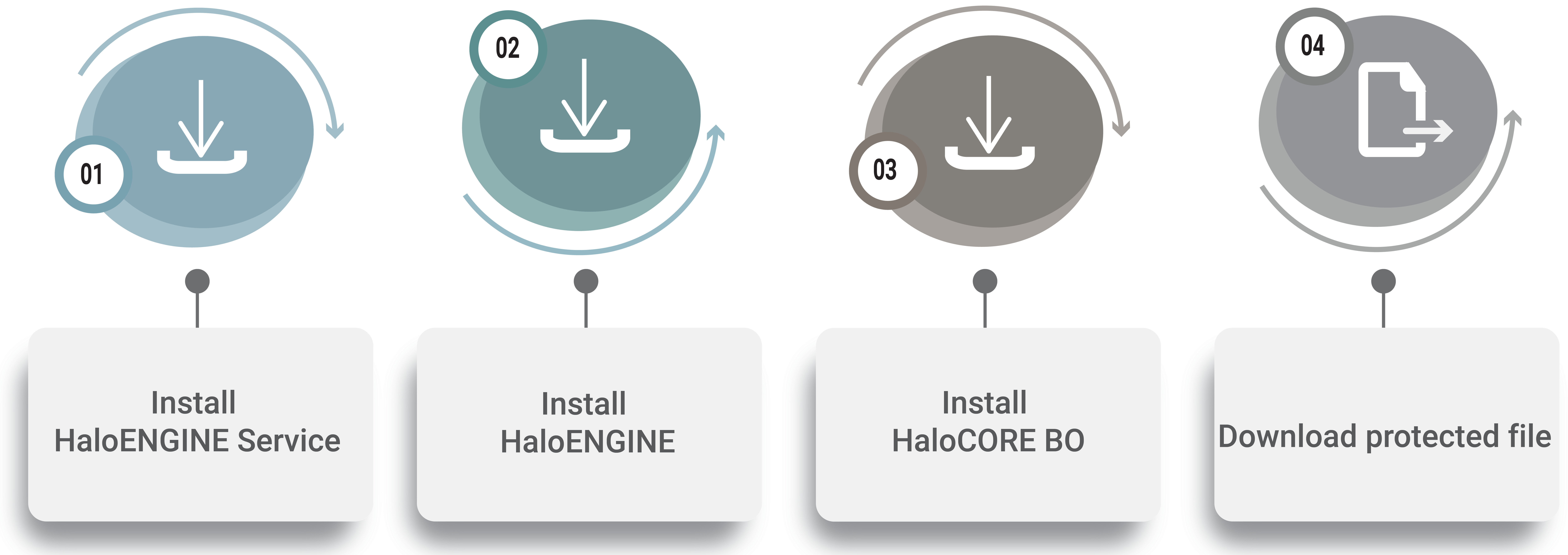
HaloCORE BO quick start installation steps
Reference Manual
Before you can work with BO, you must read the following manuals and install the components in the given order.
Document | Description |
|---|---|
HaloENGINE Installation Manual | Provides software considerations and installation procedures for HaloENGINE in your landscape. Please note that HaloCORE BO 6.4 is only compatible with HaloENGINE 6.7. |
Reference manuals
System Requirements
The following table lists the requirements for HaloCORE BO.
Requirements | Details |
|---|---|
SAP BusinessObjects Business Intelligence platform | BO 4.3 SP03 |
Requirements
Installation and Configuration

Restricted Content
Some sections of our documentation portal are exclusively available to licensed customers. If you are a licensed user, please log in to https://tech.secude.com to continue.
Why Restricted Access?
We believe in empowering our licensed customers with premium, in-depth materials to enhance their experience with our products. This ensures that our valued customers receive top-tier support and stay ahead with the most up-to-date information.
Interested in Gaining Full Access?
Our sales team is ready to assist you if you are not yet a licensed customer. Explore how our products and services can add value to your business. Contact us today to learn more about licensing options and benefits.
HaloENGINE Configuration
Follow the below procedure to create bo_config.properties.
Extract the
halo-engine-tools-<version>.zipfile, which comes along with the installation package.Open a Command Prompt window with administrator rights and navigate to the
halo-engine-tools-<version>\bin.Execute the following:
For English −
halo-engine-tools.bat EN setupBOConfigFor German −
halo-engine-tools.bat DE setupBOConfig
For Illustration purposes, the English language is used here.
|
|---|
Please refer to the below table for more details on the bo_config.properties.
Parameters | Details |
|---|---|
HaloENGINE Connection | Refers to the HaloENGINE host IP address. |
Log Locale | Refers to the language of the system error log, EN for English or DE for German. |
Keystore name | Refers to the filename of the client |
Certificate key password | Refers to the client Keystore's password. |
Certificate store password | Refers to the password of the Keystore. |
Log level | Refers to the log level - DEBUG, INFO, ERROR, WARN, and ALL. The default level is INFO. |
Client UID | Refers to System Unique ID, entered in the HaloENGINE Admin Portal. |
Customer Name |
|
Blocker file name |
|
Ignore System abort |
|
Properties
Operating Instructions
This section outlines key operations procedures for working with HaloCORE BO.
Create a Classification Profile
Step 1: Configure classification properties and their values.
Step 2: Configure PII or Financial Information for certain tcodes. (optional)
Create and configure Custom Pre-Expressions based on Client Metadata types (optional).
Create classification rules based on metadata types and Pre-Expression.
Step 3: Create Action rules to indicate if a download needs to be blocked, labeled, or protected.
Step 4: Assign systems to the profile.
Step 5: Make sure that you have configured the HaloENGINE local log and monitor properties.
How does it Work?
Functions:
Logs all data download and extraction activity from WebI and Crystal reports.
Classifies, labels, and protects data as defined in HaloENGINE.
Blocks downloading data.
Please note that E-mail, Scheduling, and Publication are not supported.
Prerequisites:
Configure rule in HaloENGINE.
HaloENGINE Service must be installed and configured in label-driven protection (MPIP) mode/protection mode. When configuring the action rule (protect) in the admin portal, HaloENGINE consumes the cached templates from HaloENGINE Service and displays them for selection.
HaloCORE BO must be installed and configured.
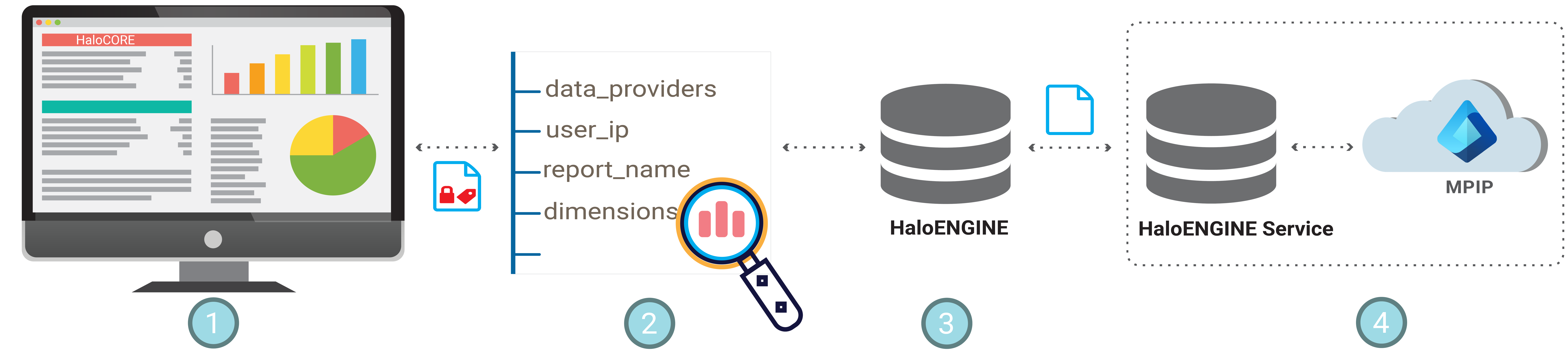
HaloCORE BO
The user extracts data.
HaloCORE BO runs in the background to collect the requested metadata and sends it to HaloENGINE. For example,
user_name = JOHN
measures = Margin, Quantity sold, Sales Revenue
queries = dataroot/variance_xtab
custom preexpression_PII = Yes
Based on collected data and derived classification, HaloENGINE determines the actions (like block/protect) to be executed on the file.
If action = label and protect, the file is embedded with derived metadata and is encrypted with a template by HaloENGINE Service, and the exported file is saved in the user-specified location. If action = block. The download is blocked with a message.
Illustration
Protected Data Download
To download data, proceed as follows:
Login to your SAP BusinessObjects BI launchpad
[http://[FQDN]:[port]/BOE/BI]. For example,http://svlu0443.secude-sap.com:8080/BOE/BI.
SAP BOBI
Click Crystal Reports or Web Intelligence icon.
For illustration purposes, Web Intelligence is shown here:
File download
You can export a report as PDF, XML, Excel, CSV, and Text files.
The following picture shows an example of HaloCORE BO in action on a client computer. In this example, the administrator has configured the action (label + protection) rules that contain the query "variance_xtab" in the Classification Engine. When the user saves a workbook that contains this data query, the file is labeled and protected. Once the file is protected, you may see a restriction banner displayed at the top of the file. Click View Permission to see the actual permissions that are applied to the file. The label that is added to the file is shown in cleartext.
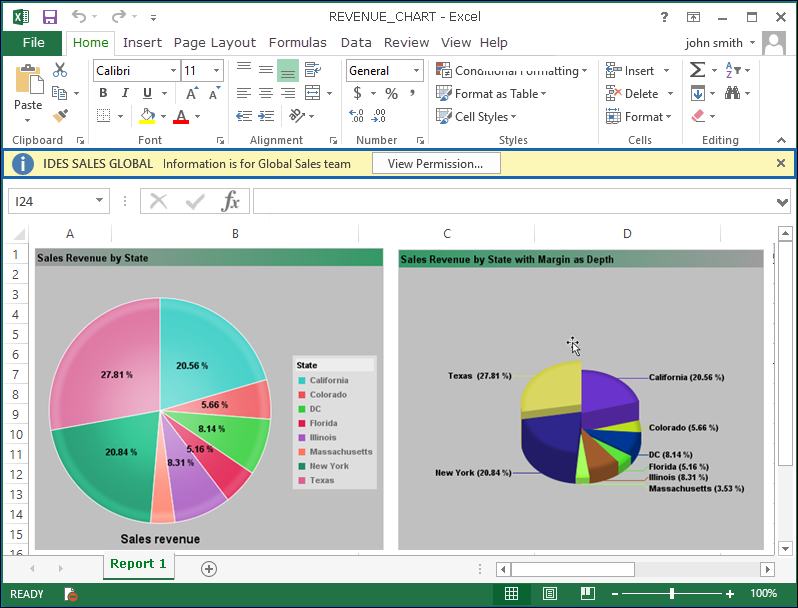
Protected file download
In this example, the administrator has configured the blocking rules.
When the user saves a report, depending on the configuration, either the default
Blocker.txtfile or the customBlocker.FileName.txt(e.g.,Blocker_ABC.txt) file is downloaded instead of the actual report.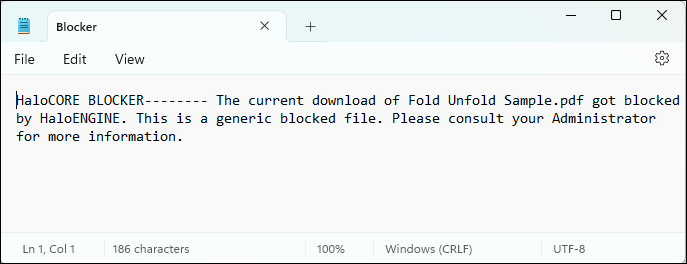
Generic blocking message #1
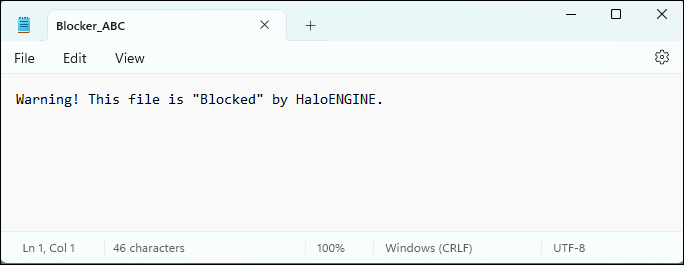
Sample of custom blocking message #2
In strict mode (
ignoreSystemAbort=false), if there is an error during the process, thenAborted.txtfile will be downloaded.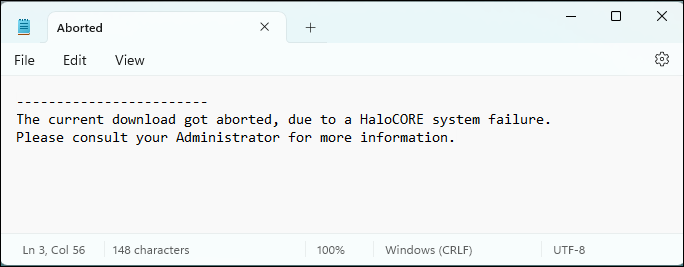
IgnoreSystemAbort
In non-strict mode (
ignoreSystemAbort=true), the normal file will be downloaded.
Unprotected Data Download
If there is a need to download a file without protection when HaloCORE is deployed in your environment, you can do so by:
Log in to the HaloENGINE Admin Portal using the super admin account.
Disable the Classification Engine.
Restart the Halo Core Tomcat Service.
Open a new Web Intelligence or Crystal Reports
Extract data and specify a location to save the file.
The file is successfully downloaded without label and protection.
Customer Support
Please be ready with the below-listed information before contacting our team to help you with the issue you are experiencing. The data that you provide will help us to serve you better.
Full contact details.
HaloCORE BO, HaloENGINE and HaloENGINE Service build version.
Date, time, and description of the error (if possible, provide screenshots).
What (if any) third-party products (software or other) were used in conjunction with our product?
Any other information necessary to reproduce the error.
Secude offers help and support through
Technical support email: support@secude.com
If you choose the email option to contact us, please provide your company details with a detailed description of the issue and attach the log file (if any). Our representative will respond to your email inquiry.Phone support: Call +41 41 510 70 70 to talk to our representative to diagnose and resolve the technical problem.
Other resources
Please visit https://secude.com to know about upcoming events, press releases, and to download whitepapers.
Documentation Feedback
Secude understands the importance of technical content when attempting to gain product knowledge and strives to continuously improve product documentation to ensure that users receive the information they want. To provide feedback on the documentation, please send an email to documentation@secude.com. Please include the following details in your feedback:
Product name and version
Documentation topic
Details of the suggestion or error
The technical documentation team will consider your feedback and address it in future documentation updates.
Appendix
Appendix 1 - Metadata
The BO metadata present in the HaloENGINE is listed in the table below.
BO metadata | Use |
|---|---|
data_providers | Derivation from the information provider. (For example, 2O0HCM_ERC_T09) |
user_ip | Derivation from user IP addresses. (For example, 10.91.0.nnn...) |
user_name | Derivation from individual users. (For example, John and Derek) |
group_names | Derivation from groups. (For example, Everyone, Administrators, and Cryptographic Officers) |
bics_names | Names of the BI consumer Service. |
xml_schema | Derivation from XML schema. |
queries | Derivation from queries. (For example, |
bex_query_tech_names | Technical names of the bex queries used. |
folder_path | Derivation from the file path. (For example, /Web Intelligence Samples) |
table_field | Derivation from field. |
measures | Derivation from measures. (For example, Margin, Quantity sold, Sales revenue) |
xml_res | Derivation from XML. (For example, |
excel_source_names | Is only used for WebI, when based on an Excel document, lists the names of the Excel source (without extension). |
universes | Derivation from universes. (For example, eFashion], group_names\=[Everyone, Administrators, Cryptographic Officers) |
report_name | Derivation from the report. |
data_system_ip | NetWeaver application server's IP address. |
dimensions | Derivation from dimensions. (For example, Lines, Quarter, State, and Year) |
excel_source_folder_paths | Derivation from Excel source location (only for WebI documents). |
preexpression_custom_pre-expression | Derivation from custom pre-expression.
|
BO metadata
Appendix 2 - Open-source Software
Third-party software/code is included or bundled with Secude's products according to its appropriate license. Secude conducts testing to make sure the third-party products are compatible with and perform as intended with Secude applications.
The third-party libraries and dependencies used by HaloCORE BO are shown in the table below.
Library | Version | Source Code | License Name | License Link |
|---|---|---|---|---|
javax.xml.bind:jaxb-api | 2.3.1 | CDDL-1.0 | ||
javax.xml.ws:jaxws-api | 2.3.1 | CDDL-1.0 | ||
javax.annotation:javax.annotation-api | 1.3.2 | CDDL-1.0 | https://github.com/javaee/javax.xml.soap/blob/master/LICENSE | |
com.sun.activation:javax.activation-api | 1.2.0 | https://repo1.maven.org/maven2/javax/activation/javax.activation-api/1.2.0/ | CDDL-1.0 | https://github.com/javaee/activation/blob/master/LICENSE.txt |
com.sun.activation: jakarta.activation | 1.2.2 | CDDL-1.0 | ||
javax.activation:activation | 1.1 | CDDL-1.0 | https://github.com/javaee/activation/blob/master/LICENSE.txt | |
org.slf4j:slf4j-api | 1.7.36 | MIT | ||
com.sun.xml.bind:jaxb-impl | 2.3.5 | CDDL-1.1 | ||
jakarta.xml.bind:jakarta.xml.bind-api | 2.3.3 | BSD 3 | https://github.com/eclipse-ee4j/jaxb-api/blob/master/LICENSE.md | |
joda-time:joda-time | 2.12.7 | Apache 2.0 | https://github.com/JodaOrg/joda-time/blob/master/LICENSE.txt | |
net.iharder:base64 | 2.3.9 | Public Domain | ||
ch.qos.logback:logback-classic | 1.2.13 | LGPL 2.1 | ||
ch.qos.logback:logback-core | 1.2.13 | LGPL 2.1 | ||
org.apache.commons:commons-lang3 | 3.13 | Apache 2.0 | https://github.com/apache/commons-lang/blob/master/LICENSE.txt | |
org.apache.logging.log4j:log4j-api | 2.20.0 | Apache 2.0 | https://github.com/apache/logging-log4j2/blob/release-2.x/LICENSE.txt | |
javax.servlet:javax.servlet-api | 4.0.1 | CDDL-1.0 | ||
com.fasterxml.jackson.core:jackson-databind | 2.13.5 | Apache 2.0 | https://github.com/FasterXML/jackson-databind/blob/2.13/LICENSE | |
org.json:json | 20211205 | org.JSON | ||
org.apache.cxf:cxf-rt-ws-rm | 3.2.14 | Apache 2.0 | ||
org.apache.cxf:cxf-rt-frontend-jaxws | 3.2.14 | Apache 2.0 | ||
org.apache.cxf:cxf-rt-rs-security-cors | 3.2.14 | Apache 2.0 | ||
com.sun.xml.ws:rt | 2.3.0 | https://jar-download.com/artifacts/com.sun.xml.ws/rt/2.3.0/source-code | EDL 1.0 | |
com.sun.xml.ws:jaxws-ri | 2.3.7 | EDL 1.0 | https://github.com/eclipse-ee4j/metro-jax-ws/blob/master/LICENSE.md | |
org.springframework: spring-context | 5.3.33 | https://github.com/spring-projects/spring-framework/tree/main/spring-context | Apache 2.0 | https://github.com/spring-projects/spring-framework/blob/main/src/docs/dist/license.txt |
org.springframework:spring-web | 5.3.33 | https://github.com/spring-projects/spring-framework/tree/main/spring-web | Apache 2.0 | https://github.com/spring-projects/spring-framework/blob/main/src/docs/dist/license.txt |
javax.resource:javax.resource-api | 1.7.1 | CDDL-1.0 | https://github.com/javaee/javax.resource/blob/master/LICENSE | |
commons-io:commons-io | 2.11.0 | Apache 2.0 | https://github.com/apache/commons-io/blob/master/LICENSE.txt | |
commons-fileupload:commons-fileupload | 1.2.1 | Apache 2.0 | https://github.com/apache/commons-fileupload/blob/master/LICENSE.txt | |
jakarta.mail:jakarta.mail-api | 1.6.7 |
| https://github.com/jakartaee/mail-api/blob/master/LICENSE.md |
Open-source software
