Appendix
This section provides supplemental information.
Supported FMS Configurations
Teamcenter supports various FMS configurations based on the volume of files to be stored, how often files are accessed by clients, and client geographical location (remote).
For illustration purposes, the supported configurations are listed below:
Single FSC
With single volume – Typically for simple deployment. Teamcenter provides a single FSC that mounts a single volume. In this case, enter the URL in the "FMS Target URL".
With multiple volumes – A standard small or medium deployment with a large volume of file storage. In this case, each volume will have an entry under this FSC. Here, enter the URL in the "FMS Target URL" field.
A sample of the FMS master file is shown below for illustration purposes:
<fscgroup id="mygroup"><loadbalancer id="ReverseProxy" address="http://SAMPLE.local:8080/tc/fms" /><fsc id="FSC_SAMPLE_Teamcenter_3" address="http://SAMPLE.local:4544" ismaster="true"><volume id="9c1cfc281ec644eabec6" enterpriseid="-1234567890" root="C:\Program Files\Siemens\volume" priority="0" /><transientvolume id="v6ca776c74e437d98ef662ecb5751tt" enterpriseid="-1234567890" root="C:\\Temp\\transientVolume_Teamcenter" /></fsc>
Multiple FSCs with Multiple Volumes – Numerous files are accessed simultaneously by the clients from more than one FSC or a single file from any one of the configured FSC. For instance, in the below case, a client is configured to connect with more than one FSC. Therefore, you must specify the details in the Other Target URL field.
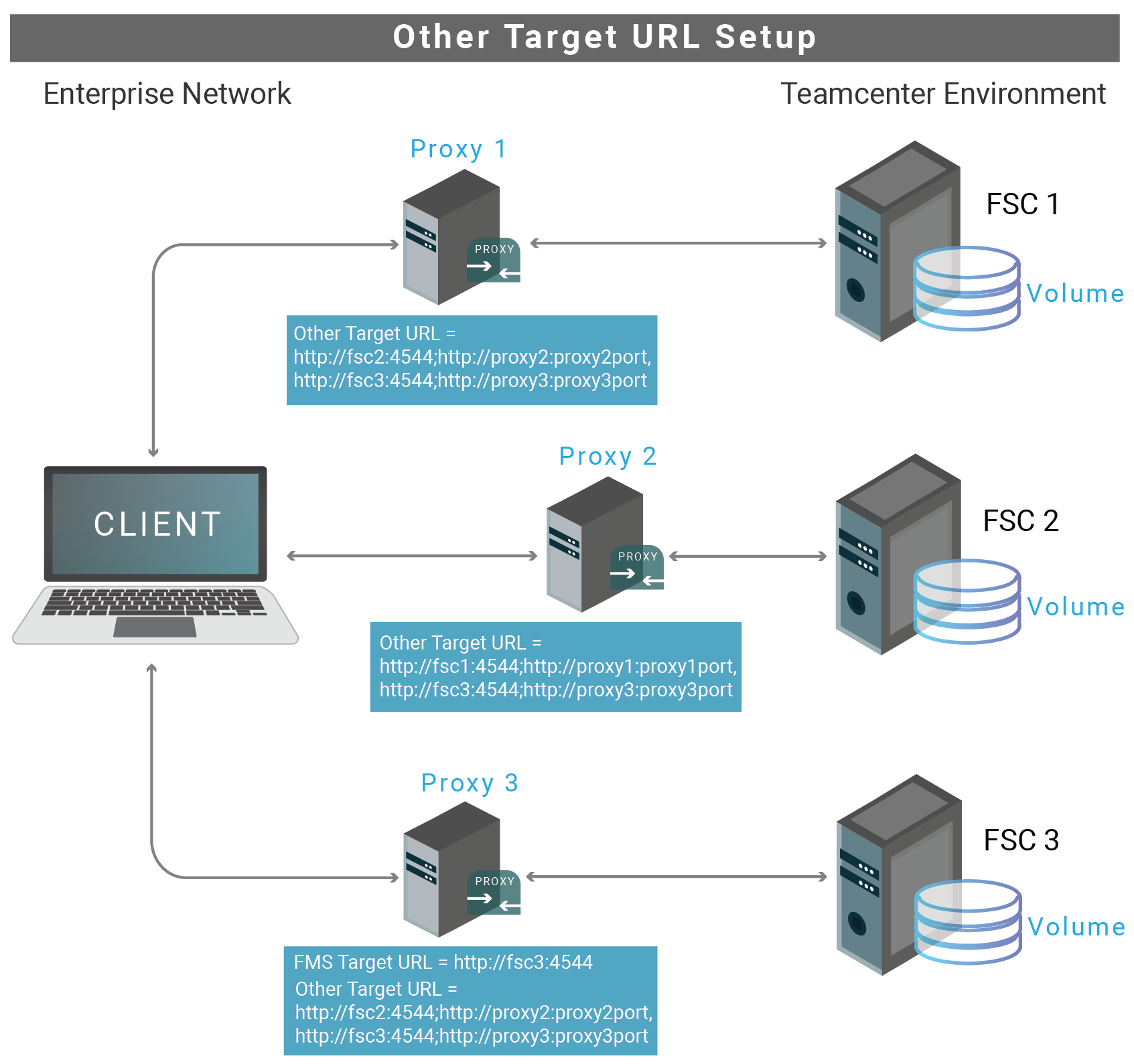
Other Target URL Setup
A sample of the FMS master file is shown below for illustration purposes:
CODE<fscgroup id="mygroup"> <loadbalancer id="ReverseProxy" address="http://PUN-FMS:8080/tc/fms"/> <fsc id="PUN-FMS_usprd01" address="http://PUN-FMS:4544" ismaster="true"> <volume id="123d0000000f8c9bd0d7" enterpriseid="-1234567890" root="E:\Siemens\usprd01_vols\dba_vol1" priority="0" /> <volume id="456a000001388c9bd0d7" enterpriseid="-1234567890" root="E:\Siemens\usprd01_vols\lyn_vol1" priority="0" /> <volume id="7898001339268c9bd0d7" enterpriseid="-1234567890" root="F:\Siemens\usprd01_vols\dba_vol2" priority="0" /> <volume id="0123001339268c9bd0d7" enterpriseid="-1234567890" root="F:\Siemens\usprd01_vols\lyn_vol2" priority="0" /> <transientvolume id="7f16bd0578697f1eb1bbb4b5020aadef" enterpriseid="-1234567890" root="D:\\Temp\\transientVolume_usprd01" priority="0" /> </fsc> <fsc id="PUN-FMS_YUN_WEB20P_usprd01" address="http://PUN-FMS-WEB:4544" ismaster="false"> <transientvolume id="8c425ee7352a4657ac777dc198712cb3" enterpriseid="-1234567890" root="D:\\Temp\\transientVolume_usprd01" priority="0" /> </fsc> <fsc id="PUN-FMS_YUT_usprd01" address="http://PUN-FMS-YUT:4544" ismaster="true"> <volume id="c07e4bfa95a44a0894b0" enterpriseid="-1234567890" root="D:\Siemens\usprd01_vols\YUT_vol1" priority="0" /> </fsc> <fsc id="PUN-FMS_YRT_usprd01" address="http://PUN-FMS-YRT:4544" ismaster="true"> <volume id="9c1cfc281ec644eabec6" enterpriseid="-1234567890" root="D:\Siemens\usprd01_vols\YRT_vol1" priority="0" /> </fsc> <clientmap subnet="127.0.0.1" mask="0.0.0.0"> <assignedfsc fscid="PUN-FMS_YUN_WEB20P_usprd01" priority="0" /> </clientmap> </fscgroup>
Failover Mechanism for HaloENGINE in HaloCAD for PLM
Server failover between two systems supports uninterrupted operation and service reliability in case of a breakdown. The server failover configuration is "active-standby," meaning that the primary server is "active", and the secondary server is "standby."
HaloCAD for PLM supports connection failover between two HaloENGINEs. Here's a summary of its purpose:
High Availability: If the primary HaloENGINE fails, the secondary HaloENGINE will take over, reducing downtime and maintaining continuous operation.
Example: Let us assume that your business process requires no downtime.
As per the business security policy, your administrator has configured Fail-Safe Mode as Strict to block any file upload or download whenever an error occurs. If HaloENGINE encounters an unexpected issue, failure to obtain label information will prevent file download or upload. In this instance, the failover mechanism in HaloENGINE will be the ideal option for dealing with such unforeseen scenarios, with no impact on the end user. Thus, even if the primary HaloENGINE connection fails, HaloCAD recognizes the failure and instantly switches to the secondary HaloENGINE to continue providing services.
Once the primary HaloENGINE is restored, it will be a standby for the secondary HaloENGINE. If there is any failure in the secondary HaloENGINE, the primary HaloENGINE will again take over the operations.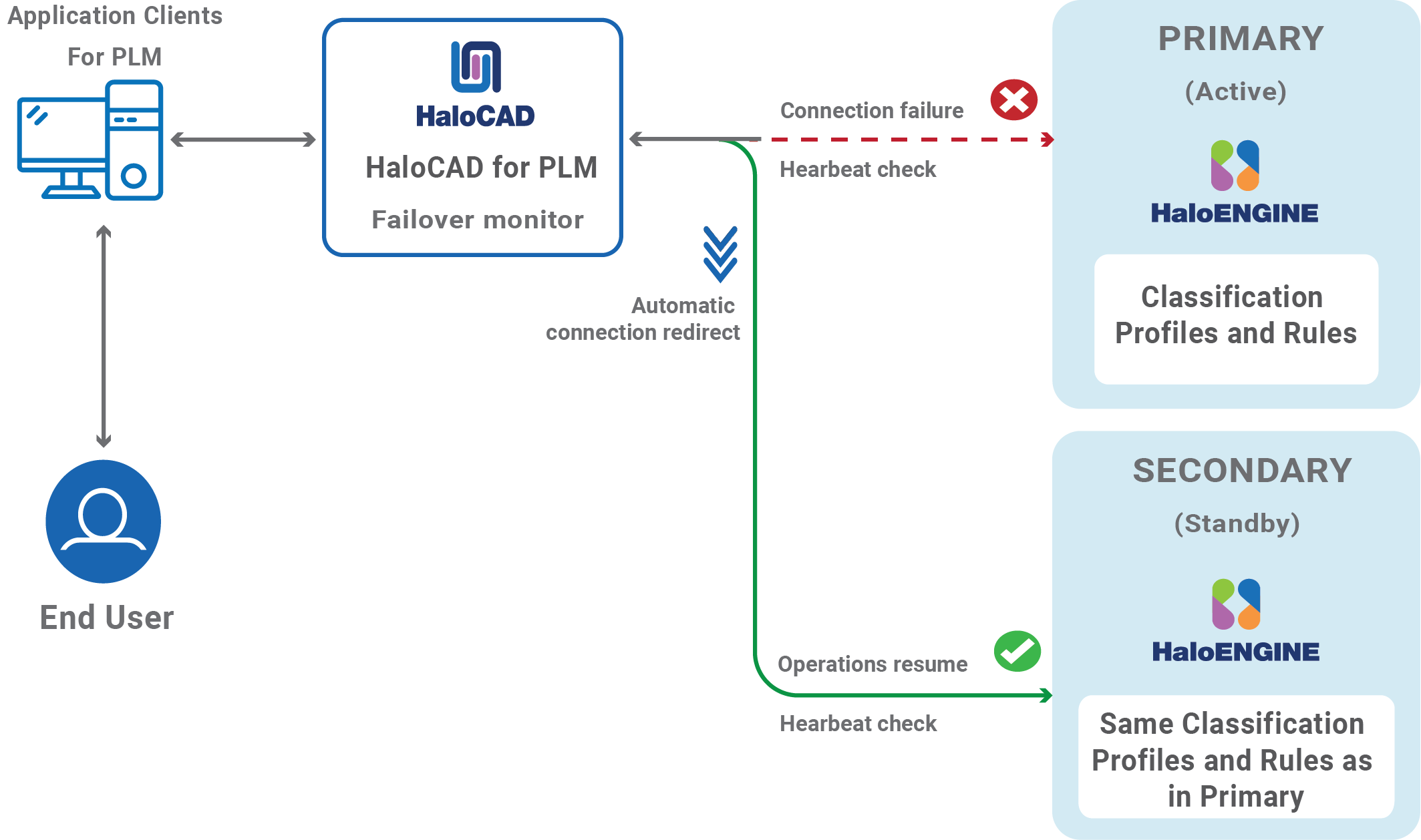
Failover Mechanism for HaloENGINE in HaloCAD for PLM
Redundancy: It provides redundancy, which means there is always another HaloENGINE ready to take over if the primary one fails. This minimizes the possibility of a single point of failure.
Data Integrity and Consistency: In the event of a failure, the failover technique can help guarantee that data is consistent and file upload/download activities are not lost, which is crucial for systems that rely on high data security.
Failover Mechanism Requirement
Network Infrastructure: Minimal Secondary HaloENGINE needs to be segmented so that the primary and secondary HaloENGINEs don't share the same network.
Make sure the secondary HaloENGINE has HaloENGINE service installed as well.
Data replication: Both HaloENGINEs must have the same classification profiles and rules.
Open-source Software
Third-party software/code is included or bundled with Secude's products according to its appropriate license. Secude conducts testing to make sure the third-party products are compatible with and perform as intended with Secude applications.
The third-party libraries and dependencies used by HaloCAD for Teamcenter are shown in the table below.
Library | Version | Source Code | License Link |
|---|---|---|---|
HTTP-Proxy-Servlet | https://github.com/mitre/HTTP-Proxy-Servlet/blob/master/LICENSE.txt | ||
httpmime | 4.5.+ | https://mvnrepository.com/artifact/org.apache.httpcomponents/httpmime | |
httpclient | 4.5.+ | https://mvnrepository.com/artifact/org.apache.httpcomponents/httpclient | |
javax.mail | 1.5.+ | http://www.sun.com/cddl | |
commons-io | 2.+ | ||
javax.servlet-api | 3.1.+ | https://mvnrepository.com/artifact/javax.servlet/javax.servlet-api | |
jna | 5.6.0 | http://www.apache.org/licenses/LICENSE-2.0.txt | |
jna-platform | 5.6.0 | https://mvnrepository.com/artifact/net.java.dev.jna/jna-platform | http://www.apache.org/licenses/LICENSE-2.0.txt |
Open-source software
Metadata
The Teamcenter metadata present in the HaloENGINE is listed in the table below.
Teamcenter metadata | Use |
|---|---|
user_role | Derivation from user role. Multiple roles may be assigned to a single user. (For example, Designer and Engineer) |
user_def_group | Derivation from a group of users who log in. (For example, a user from Engineering group) |
gov_clearance | Derivation from a specific object based on value or licensing value. (For example, secret - single value field) |
ip_clearance | Derivation from intellectual property (IP) classification values and clearance levels assigned to data objects and users for IP access evaluation. (For example, super-secret - single value field) |
user_name | Derivation from Teamcenter logged-in users. (For example, John and Derek) |
file_type | Derivation from file type and Teamcenter object data. (NX file types and MS Office native file types) (For example, prt, asm, and XLSX) |
gov_classification | Derivation from a Teamcenter object based on its value or license value. (For example, secret - single value field) |
obj_project_names | Derivation from Teamcenter object data. The object could be used in several projects. (For example, project1; project2- multi-value- field) |
ip_classification | Derivation from Teamcenter's intellectual property (IP). (For example, secret, internal, and confidential - single value field) |
preexpression_custom_pre-expression | Derivation from custom pre-expression.
|
Teamcenter metadata
Download Log Definition
This section explains the log definition for every log format that HaloENGINE supports.
What is SIEM Integration?
SIEM, which stands for Security Information and Event Management, is a comprehensive approach to managing an organization's security information and events. SIEM integration refers to the process of incorporating SIEM solutions into an organization's existing IT infrastructure to enhance its ability to monitor, detect, and respond to security incidents. To support this approach, HaloENGINE transmits logs in JavaScript Object Notation (JSON), Log Event Extended Format (LEEF), and Common Event Format (CEF).
Common Event Format is an open log management standard developed by HP ArcSight. CEF comprises a standard prefix and a variable extension that is formatted as key-value pairs.
Log Event Extended Format is a customized event format for IBM Security QRadar. LEEF comprises a LEEF header, event attributes, and an optional Syslog header.
JavaScript Object Notation is a lightweight text-based open standard designed for human-readable data interchange.
These logs are forwarded to the communications module, which transmits them to your collection server via UDP or TCP. Ideally, a SIEM (Microsoft Azure Sentinel, Splunk, RSA, and others) server would scan the received messages, sort them, and alert your security team.

Forwarding logs
Why CEF Standard?
The CEF format is an open log management standard that simplifies log management. CEF allows third parties to create their device schemas that are compatible with a standard that is used industry-wide for normalizing security events. Technology companies and customers can use the standardized CEF format to facilitate data collection and aggregation, for later analysis by an enterprise management system. CEF is an extensible, text-based format designed to support multiple device types by offering the most relevant information. It defines the syntax for log records consisting of a standard header and a variable extension, formatted as key-value pairs.
Syslog and CEF Header
The data is normalized and categorized into the ArcSight CEF for easy correlation and analysis. CEF uses Syslog as a transport mechanism. It uses the following format, consisting of a Syslog prefix, a header, and an extension, as shown below. If an event producer is unable to write Syslog messages, it is still possible to write the events to a file.
|
CEF format
|
CEF format sample
Format | Description | Example |
|---|---|---|
Prefix | Syslog applies a prefix to each message, no matter which device it arrives from, that contains the date and hostname. |
|
Header | Version is an integer and identifies the version of the CEF format. The current CEF version is 0 (CEF:0). |
|
Device Vendor, Device Product, and Device Version are strings that uniquely identify the type of sending device. |
| |
|
| |
Extension | The Extension field contains a collection of key-value pairs. The keys are part of a predefined set. The standard allows for including additional keys as outlined in "ArcSight Extension Dictionary”. An event can contain any number of key-value pairs in any order, separated by spaces (""). If a field contains a space, such as a filename, this is valid and can be logged in exactly that manner. Secude uses only Standard Key Names from ArcSight Extension Directory and no custom extensions. The reason for that is to avoid significant limitations custom extensions will cause. | Please refer to the following table. |
CEF Header details
|
CEF sample
Why LEEF Standard?
The Log Event Extended Format (LEEF) is a customized event format for IBM Security QRadar that contains readable and easily processed events for QRadar.
Syslog and LEEF Header
The LEEF format consists of a Syslog header, a LEEF header, and event attributes. The Syslog header is an optional field. The Syslog header contains the timestamp and IPv4 address or hostname of the system that sends the event. The LEEF header is a required field for LEEF events. The LEEF header is a pipe delimited (|) set of values that identifies your software or appliance to QRadar. Event attributes identify the payload information of the event that is produced by your appliance or software. Every event attribute is a key-value pair with a tab that separates individual payload events.
|
LEEF format
|
|---|
LEEF format sample
Format | Description | Example |
|---|---|---|
Syslog Header | The Syslog header contains the timestamp. |
|
LEEF Header | LEEF:version | An integer value that identifies the major and minor version of the LEEF format that is used for the event, for example,
|
Product name | A text string that identifies the product that sends the event log to QRadar, for example, | |
Product version | A string that identifies the version of the software or appliance that sends the event log, for example,
| |
EventID | A unique identifier for an event. | |
Delimiter Character | Pipe Specifies an alternative delimiter to the attributes. You can use a single character or the hex value for that character. The hex value can be represented by the prefix 0x or x, followed by a series of 1-4 characters (0-9A-Fa-f). | |
Event Attributes | Predefined Key Entries | A set of key-value pairs that provide detailed information about the security event. Each event attribute must be separated by a tab or the delimiter character, but the order of attributes is not enforced. |
LEEF Header details
Why JSON Standard?
The JSON format is a lightweight text-based interchange format used for serializing and transmitting structured data over the network connection. Furthermore, it supports Security Information and Event Management solutions (e.g., Microsoft Azure Sentinel, Splunk, etc.,) seamlessly.
JSON syntax is considered as a subset of JavaScript syntax; it includes the following:
Data is represented in name/value pairs.
Curly braces hold objects and each name is followed by ':'(colon), the name/value pairs are separated by ','(comma).
Square brackets hold arrays and values are separated by ','(comma).
|
JSON format
Deactivating the HaloCAD for Teamcenter
For any diagnostic testing purposes in connection with HaloCAD, you may need to deactivate the HaloCAD for a while. In such cases, follow the below procedure:
Step 1. Stop fsc service.
Remove the changes done in FMS master file
fmsmaster_FSC_<ComputerName>_Teamcenter.xmlFor example,
<loadbalancer id="ReverseProxy" address="http://tclu0310.Secude.local:8080/tc/fms/" />Step 2. Remove the changes made in the FCC file.
Go to
<installed_path>\Teamcenter12\tccs\bin>, and execute CMD with administrator privilege.Type
fccstat.exe -stopand press Enter.Remove the changes at the line in the
fcc.xmlfile.FCC Line format:
<parentfsc address="http://:/tc/fms" priority="0" transport="lan"/> <assignment address="parentfsc address">Alternatively, you use the backup files of these two.
Step 3. Start fsc service.
Type
fccstat.exe -startand press Enter.Type
fccstat.exe -statusand press Enter. You will receive a confirmation message without the Haloproxy port number, which confirms that HaloCAD is not active.
Step 4. Remove the two system variables - Default_Transient_Server and Fms_BootStrap_Urls.
Step 5. Restart Server Manager from
services.msc.Complete your investigation and then activate it, as described in the section “TCCS Configuration - Step 2”.
Uninstalling the HaloCAD for Teamcenter
Once you stop using the HaloCAD component, you can uninstall it. Uninstall removes all files and registry settings that were added to your computer at the time of initial installation.
Prerequisite: Make sure to close the configuration tool before performing uninstallation. Otherwise, an error message will appear such as "Kindly close the running config tool and proceed uninstallation!"
Method #1
Click Start menu > go to Control Panel > Programs > Programs and Features > Uninstall a Program > select HaloCAD for Teamcenter application from the list > right-click and select Uninstall option or double-click on the installer
HaloCAD_Teamcenter_Setup.exefile.Depending on your Windows security settings, you may get a security warning as "Do you want to allow the following program to make changes to this computer?". If you get this security warning, click the Yes button to confirm that you want to uninstall the HaloCAD component.
The following confirmation message will appear.
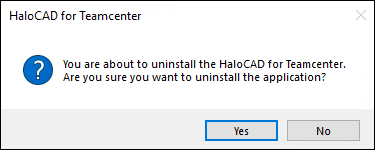
Uninstall Message #1
Click Yes to confirm that you want to remove it from the computer.
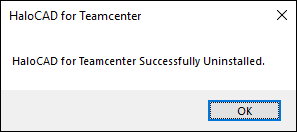
Uninstall Message #2
The HaloCAD component has been successfully uninstalled. Click OK to close the dialog.
The uninstalling process is complete.
Method #2
The HaloCAD component can be removed using the command line, as illustrated in the sample below.
Open a command prompt.
Navigate to the HaloCAD component's directory.
Example:HaloCAD_Teamcenter_Setup.exe -uninstallThe uninstalling process is complete.
